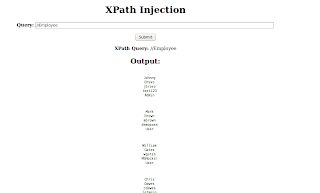
XPath is a language that has been designed and developed to operate on data that is described with XML. The XPath injection allows an attacker to inject XPath elements in a query that uses this language. Some of the possible goals are to bypass authentication or access information in an unauthorized manner.
We are gonna learn using simple example. Download code from here & put it in your local server directory.(Code is created by Amol Naik )
Sample XML Document which we gonna use:-
<Employees>
<!-- Employees Database -->
<Employee ID="1">
<FirstName>Johnny</FirstName>
<LastName>Bravo</LastName>
<UserName>jbravo</UserName>
<Password>test123</Password>
<Type>Admin</Type>
</Employee>
<Employee ID="2">
<FirstName>Mark</FirstName>
<LastName>Brown</LastName>
<UserName>mbrown</UserName>
<Password>demopass</Password>
<Type>User</Type>
</Employee>
<Employee ID="3">
<FirstName>William</FirstName>
<LastName>Gates</LastName>
<UserName>wgates</UserName>
<Password>MSRocks!</Password>
<Type>User</Type>
</Employee>
<Employee ID="4">
<FirstName>Chris</FirstName>
<LastName>Dawes</LastName>
<UserName>cdawes</UserName>
<Password>letmein</Password>
<Type>User</Type>
</Employee>
</Employees>
We are gonna learn using simple example. Download code from here & put it in your local server directory.(Code is created by Amol Naik )
Sample XML Document which we gonna use:-
<Employees>
<!-- Employees Database -->
<Employee ID="1">
<FirstName>Johnny</FirstName>
<LastName>Bravo</LastName>
<UserName>jbravo</UserName>
<Password>test123</Password>
<Type>Admin</Type>
</Employee>
<Employee ID="2">
<FirstName>Mark</FirstName>
<LastName>Brown</LastName>
<UserName>mbrown</UserName>
<Password>demopass</Password>
<Type>User</Type>
</Employee>
<Employee ID="3">
<FirstName>William</FirstName>
<LastName>Gates</LastName>
<UserName>wgates</UserName>
<Password>MSRocks!</Password>
<Type>User</Type>
</Employee>
<Employee ID="4">
<FirstName>Chris</FirstName>
<LastName>Dawes</LastName>
<UserName>cdawes</UserName>
<Password>letmein</Password>
<Type>User</Type>
</Employee>
</Employees>
Bypass Authentication:-
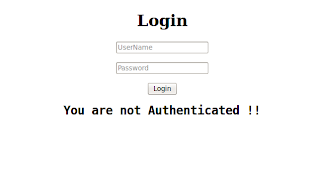
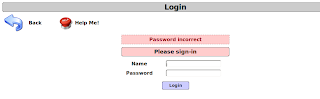
Browse to the login.php page; here we can see simple login form.
If the application does not properly filter such input, the tester will be able to inject XPath code and interfere with the query result. For instance, the tester could input the following values:
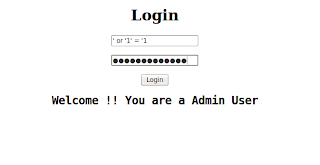
Username: ' or '1' = '1
Password: ' or '1' = '1
Looks quite familiar, doesn't it? Using these parameters, the query becomes:
string(//Employee[uname/text()='' or '1' = '1' and passwd/text()='' or '1' = '1']/account/text())
As in a common SQL Injection attack, we have created a query that is always evaluated as true, which means that the application will authenticate the user even if a username or a password have not been provided.
Blind Xpath Injection:-
If there is no knowledge about the XML data internal details and if the application does not provide useful error messages that help us reconstruct its internal logic, it is possible to perform a Blind XPath Injection attack whose goal is to reconstruct the whole data structure.
Browse to the search.php page. Enter any number, When you provide number it will display FirstName related to their ID.
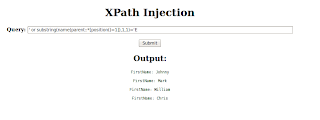
Enter ' or '1' = '1 in search , & you will get all FirstName regardless of any ID(Number).
In blind Xpath injection we have to provide special crafted query to application, if query is true we will get result otherwise we will not get any result.Till now We don`t know about any parent or child node of XML document.
Guessing of parent node:-
Supply following query to application & observe result.
' or substring(name(parent::*[position()=1]),1,1)='a
Nothing append , we don`t get FirstName of users.It means first letter of parent node is not "a". Now supply following query
' or substring(name(parent::*[position()=1]),1,1)='E
You get result , It means first letter of parent node is "E"
To guess second letter of parent node supply following query
' or substring(name(parent::*[position()=1]),2,1)='m
Following the same procedure, we can extract the full name of the parent node, which was found to be 'Employee'.
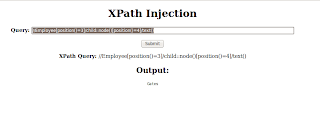
We can also get child node. Browse to the xpath.php page & enter following query.
//Employee[position()=3]/child::node()[position()=4]/text()
You got output from parent node Employee id 3 & child node whose position is 2.
To get whole document put following query.
//Employee
It`s just concept how to retrieve data from XML document using XPATH injection.XPath contains two useful functions that can help you automate the preceding attack and quickly iterate through all nodes and data in the XML document:
- count() returns the number of child nodes of a given element, which can be used to determine the range of position() values to iterate over.
- string-length() returns the length of a supplied string, which can be used to determine the range of substring() values to iterate over.
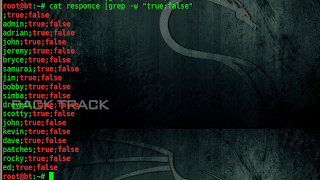
I used recon-ng xpath bruteforcer for xpath injection attack & we will get back end XML file.
Useful Links & Blind XPATH injection Tools:-
https://www.owasp.org/index.php/XPATH_Injection
https://www.owasp.org/index.php/Blind_XPath_Injection
XPATH BLIND EXPLORER:- http://code.google.com/p/xpath-blind-explorer/downloads/list
XCAT:- https://github.com/orf/xcat
Useful Links & Blind XPATH injection Tools:-
https://www.owasp.org/index.php/XPATH_Injection
https://www.owasp.org/index.php/Blind_XPath_Injection
XPATH BLIND EXPLORER:- http://code.google.com/p/xpath-blind-explorer/downloads/list
XCAT:- https://github.com/orf/xcat