Today we are going to extract password from Fireox & Thunderbird which are saved in browser and then try to decrypt that passwords from remote PC. Before some times ; i posted
here that how to extract information from saved sqlite database of skype, firefox, chrome using python script.
Most of the morden browser save information in sqlite format. When user enter login information ; firefox asked user to remember password.If user click on remember password then this passwords are saved into firefox database in signons.sqlite. But passwords are encrypted. so just by downloading signons.sqlite we can not extract passwords from it. Signons.sqlite is useless without the key3.db file, which also resides in the profile folder of your application. Passwords in the signons.sqlite file is encrypted with TripleDES in CBC mode. The key used for the encryption is saved in key3.db and encrypted as well.
Firefox Database path in windows:-
[Windows XP]
C:\Documents and Settings\<user_name>\Application Data\Mozilla\Firefox\<random_name>.default
[Windows Vista & Windows 7]
C:\Users\<user_name>\AppData\Roaming\Mozilla\Firefox\<random_name>.default
Firefox Database path in linux
/root/.Mozilla/Firefox/Profile/<random_name>.default
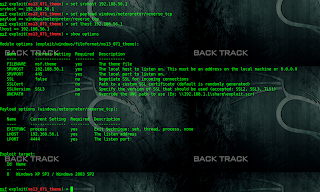
First we have to get meterpreter shell using any known vulnerability or using any
metasploit method.
Then we have to download three files from remote PC which are key3.db,signons.sqlite;cert8.db.You can use metasploit post module (use post/multi/gather/firefox_creds)for downloading this file or you can also download manually by browsing directory.
Now we have database file as well as encryption key in key3.db. So now we have to decrypt it. I can not find any third party software to decrypt this passwords for linux platform.But i found one software which is working very well in windows.Download software from
here . (It will work for both Firefox & thunderbird)
(1)copy key3.db,signons.sqlite;cert8.db files in some folder which can be browse from windows.
(2)Open windows.
(3)Install that software.
(4)Open it and Just specify firefox installed path & specify folder in which we copied downloaded file.
(5)click on Start recovery button.
Fireox & thunderbird use same encryption technique. So you can also get thunderbird password from above mention method. Just download key3.db,signons.sqlite;cert8.db files from thunderbird folder whose path are as follow
[Windows XP]
C:\Documents and Settings\<user_name>\Application Data\Thunderbird\Profiles\<random_name>.default
[Windows Vista & Windows 7]
C:\Users\<user_name>\AppData\Roaming\Thunderbird\Profiles\<random_name>.default
What is solution?
If you set master password for firefox & thunderbird then without master password ; saved passwords can not be decrypted.