Portspoof is meant to be a lightweight, fast, portable, and secure addition to any firewall system or security system. The general goal of the program is to make the information-gathering phase slow and bothersome for your attackers as much as possible. This is quite a change to the standard 5s nmap scan that will give a full view of your system’s running services.
Showing posts with label Penetration Testing. Show all posts
Showing posts with label Penetration Testing. Show all posts
Wednesday, April 30, 2014
Monday, February 10, 2014
Manual Web Application Penetration Testing – Suffix & Prefix in Fuzzing
Introduction
In this series of articles, last time we talked about fuzzing and various SQL statement special characters which can be used in fuzzing a web application. In this article, I am going to focus on various prefixes and suffixes of fuzzing in order to fuzz the target web application.
CLICK HERE TO READ FULL ARTICLE
In this series of articles, last time we talked about fuzzing and various SQL statement special characters which can be used in fuzzing a web application. In this article, I am going to focus on various prefixes and suffixes of fuzzing in order to fuzz the target web application.
CLICK HERE TO READ FULL ARTICLE
Thursday, January 30, 2014
Manually Web Application Penetration Testing: Fuzzing - Part 4
Introduction
When we test a web application, we do not test a single page, but a lot of pages of a single web application. Each page may have more than one variable, so technically you will be engaging with a ton of variables during your web application test. So when you inject anything into the input, it is good to know what kind of effect your injection has on the server. In this part of this series of articles, we will look at the importance of simple alphabetic injection along with the web page encoding technology and how it affects our testing and result.
Simple Alphabetic Injection
When you engage with many web pages and a ton of variables, it is good to find your input after you inject. When you give something to the web page as an input, your input will not be used in only one place, but it will be used for many variables and tons of places. One of the common ways to check which areas use a given input is to give a simple alphabetic injection. This simple alphabetic injection can be anything. As I said in an earlier article, I personally use Jonnybravo as a username and momma as a password. If I use any special characters within my input, it might get encoded/eliminated to prevent the injection attacks on that page. What encoding is and how it takes place I will cover later on. The reason for using simple alphabetic injection is because it will never be encoded or eliminated by the server and you can easily find your input within the response as well as the request.
Monday, January 20, 2014
Manual Web Application Penetration Testing: Identifying Application Entry Points
Introduction
In this article, I will show you how to find injection points for your target host and how the webpage is encoded when it comes to the client side from the server.
Identifying Injection Points
If your web page is static, you cannot test it for security concern. You can test it at some sort of view but you can’t play with it much as compared to a dynamic page. The Nikto scanner is a good utility that works best in testing static sites. There has to be some interaction between client and server via login panel, comment section, register page, contact form, and so on.
To Read Full Article Click Here : http://resources.infosecinstitute.com/manual-web-application-penetration-testing-identifying-application-entry-points/
Friday, January 17, 2014
Manual Web Application Penetration Testing: Introduction
In this series of articles, I am going to demonstrate how you can manually exploit the vulnerability of a web application, compared to using any automation tool, in order to find vulnerabilities in the application. Almost all companies worldwide focus on manual testing of web application rather than running web application scanners, which limit your knowledge and skills and the scope of finding a vulnerability with your testing.
For the whole series I am going to use these programs:
For the whole series I am going to use these programs:
- NOWASP Mutiliadae
- BURP Proxy
Monday, July 1, 2013
PenQ: Open source Linux based penetration testing browser bundle
PenQ is an open source Linux based penetration testing browser bundle we built over Mozilla Firefox. It comes pre-configured with security tools for spidering, advanced web searching, fingerprinting, anonymous browsing, web server scanning, fuzzing, report generating and more.
PenQ is configured to run on Debian based distributions including Ubuntu and its derivative distros, and penetration testing operating systems such as BackTrack and Kali.With all its integrations, PenQ is a powerful tool. Be mindful of what use you put it to. Responsible use of PenQ can help secure web apps in a zap.
Download and more info: http://www.qburst.com/products/PenQ
PenQ is configured to run on Debian based distributions including Ubuntu and its derivative distros, and penetration testing operating systems such as BackTrack and Kali.With all its integrations, PenQ is a powerful tool. Be mindful of what use you put it to. Responsible use of PenQ can help secure web apps in a zap.
Features
- OWASP ZAP
- OWASP WebScarab
- OWASP WebSlayer
- Nikto Web Server Scanner
- Wfuzz Web Application Fuzzer
- Mozilla Add-ons Collection
- Integrated Tor
- OWASP Penetration Testing Checklist
- PenTesting Report Generator
- Vulnerability Databases Search
- Access to Shell and System Utilities
- Collection of Useful Links
Nishang v.0.2.7 Released: PowerShell for Penetration Testing
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation during Penetraion Tests. The scripts are written on the basis of requirement by the author during real Penetration Tests.It contains many interesting scripts like download and execute, keylogger, dns txt pwnage, wait for command and much more.
Changelog:
- DNS_TXT_Pwnage, Time_Execution and Wait_For_Command can now be stopped remotely. Also, these does not stop autmoatically after running a script/command now.
- DNS_TXT_Pwnage, Time_Execution and Wait_For_Command can now return results using selected exfiltration method.
- Fixed a minor bug in DNS_TXT_Pwnage.
- All payloads which could post data to the internet now have three options pastebin/gmail/tinypaste for exfiltration.
- Added Get-PassHashes payload.
- Added Download-Execute-PS payload.
- The keylogger logs only fresh keys after exfiltring the keys 30 times.
- A delay after success has been introduced in various payloads which connect to the internet to avoid generating too much traffic.
Download: http://code.google.com/p/nishang/downloads/list
Changelog:
- DNS_TXT_Pwnage, Time_Execution and Wait_For_Command can now be stopped remotely. Also, these does not stop autmoatically after running a script/command now.
- DNS_TXT_Pwnage, Time_Execution and Wait_For_Command can now return results using selected exfiltration method.
- Fixed a minor bug in DNS_TXT_Pwnage.
- All payloads which could post data to the internet now have three options pastebin/gmail/tinypaste for exfiltration.
- Added Get-PassHashes payload.
- Added Download-Execute-PS payload.
- The keylogger logs only fresh keys after exfiltring the keys 30 times.
- A delay after success has been introduced in various payloads which connect to the internet to avoid generating too much traffic.
Download: http://code.google.com/p/nishang/downloads/list
Wednesday, January 9, 2013
Blackhat USA 2012: Conference Official Recordings & Tools Released
![Blackhat USA 2012 [2012, ENG] Blackhat USA 2012 [2012, ENG]](http://i53.fastpic.ru/big/2013/0107/aa/38d7caef7e2a9bfecadaae8bc73716aa.jpg)
Blackhat USA 2012 [2012, ENG]
English | h264, yuv420p, 1200x600, 14.98 fps | aac, 44100 Hz, mono | 14.38 GB
Genre: Video Training
English | h264, yuv420p, 1200x600, 14.98 fps | aac, 44100 Hz, mono | 14.38 GB
Genre: Video Training
Here are the videos for all the sessions of Blackhat USA 2012. It also includes a few of tools released during this conference
Content
-https://www.blackhat.com/html/bh-us-12/schedule/briefings-25.html
-https://www.blackhat.com/html/bh-us-12/schedule/briefings-26.html
![Blackhat USA 2012 [2012, ENG] Blackhat USA 2012 [2012, ENG]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_vH91YcjIRcpERvgbo28fAXGN9MvaJfrDCIXSxTTliWaq9IbXrKxvVzBO6xiOxF6Hzf-xpbh89QdK6pSLU5J6958aL0jAUwI8aK7LuYrFdFWhzaeibUXkQQEbhRpOUUXBNCav4sETKfsgPSwWR2NQ=s0-d)
-https://www.blackhat.com/html/bh-us-12/schedule/briefings-25.html
-https://www.blackhat.com/html/bh-us-12/schedule/briefings-26.html
![Blackhat USA 2012 [2012, ENG] Blackhat USA 2012 [2012, ENG]](http://i54.fastpic.ru/big/2013/0107/bb/cba90d017dacd88b0f050cedc4a9a7bb.jpg)
Link Download
http://extabit.com/file/278u4dxyj4wja/blackhat-2012.part01.rar
http://extabit.com/file/278u4dxyiic9y/blackhat-2012.part02.rar
http://extabit.com/file/278u4dxyj5c8m/blackhat-2012.part03.rar
http://extabit.com/file/278u4dxyj4zna/blackhat-2012.part04.rar
http://extabit.com/file/278u4dxyj591y/blackhat-2012.part05.rar
http://extabit.com/file/278u4dxyj5ccm/blackhat-2012.part06.rar
http://extabit.com/file/278u4dxyiic92/blackhat-2012.part07.rar
http://extabit.com/file/278u4dxyj4zme/blackhat-2012.part08.rar
http://extabit.com/file/278u4dxyj52py/blackhat-2012.part09.rar
http://extabit.com/file/278u4dxyjrwk6/blackhat-2012.part10.rar
http://extabit.com/file/278u4dxyjqree/blackhat-2012.part11.rar
http://extabit.com/file/278u4dxyjrzqe/blackhat-2012.part12.rar
http://extabit.com/file/278u4dxyjrwh2/blackhat-2012.part13.rar
http://extabit.com/file/278u4dxyjrwg6/blackhat-2012.part14.rar
http://extabit.com/file/278u4dxyjqo7a/blackhat-2012.part15.rar
or
http://rapidgator.net/file/67241593/blackhat-2012.part01.rar.html
http://rapidgator.net/file/67244253/blackhat-2012.part02.rar.html
http://rapidgator.net/file/67245401/blackhat-2012.part03.rar.html
http://rapidgator.net/file/67245416/blackhat-2012.part04.rar.html
http://rapidgator.net/file/67245431/blackhat-2012.part05.rar.html
http://rapidgator.net/file/67245436/blackhat-2012.part06.rar.html
http://rapidgator.net/file/67245516/blackhat-2012.part07.rar.html
http://rapidgator.net/file/67245553/blackhat-2012.part08.rar.html
http://rapidgator.net/file/67239035/blackhat-2012.part09.rar.html
http://rapidgator.net/file/67239038/blackhat-2012.part10.rar.html
http://rapidgator.net/file/67240057/blackhat-2012.part11.rar.html
http://rapidgator.net/file/67240113/blackhat-2012.part12.rar.html
http://rapidgator.net/file/67240136/blackhat-2012.part13.rar.html
http://rapidgator.net/file/67240151/blackhat-2012.part14.rar.html
http://rapidgator.net/file/67238624/blackhat-2012.part15.rar.html
or
http://ryushare.com/256156e93b5a/blackhat-2012.part01.rar
http://ryushare.com/256156e93b5b/blackhat-2012.part02.rar
http://ryushare.com/256156e93b5c/blackhat-2012.part03.rar
http://ryushare.com/256156e93b5d/blackhat-2012.part04.rar
http://ryushare.com/256156e93b5e/blackhat-2012.part05.rar
http://ryushare.com/256156e93b5f/blackhat-2012.part06.rar
http://ryushare.com/273300334cda/blackhat-2012.part07.rar
http://ryushare.com/264a2b8e3c60/blackhat-2012.part08.rar
http://ryushare.com/256156e93b57/blackhat-2012.part09.rar
http://ryushare.com/264a2b8e3c61/blackhat-2012.part10.rar
http://ryushare.com/256156e93b58/blackhat-2012.part11.rar
http://ryushare.com/273300334cdc/blackhat-2012.part12.rar
http://ryushare.com/264a2b8e3c62/blackhat-2012.part13.rar
http://ryushare.com/264a2b8e3c63/blackhat-2012.part14.rar
http://ryushare.com/256156e93b59/blackhat-2012.part15.rar
http://extabit.com/file/278u4dxyj4wja/blackhat-2012.part01.rar
http://extabit.com/file/278u4dxyiic9y/blackhat-2012.part02.rar
http://extabit.com/file/278u4dxyj5c8m/blackhat-2012.part03.rar
http://extabit.com/file/278u4dxyj4zna/blackhat-2012.part04.rar
http://extabit.com/file/278u4dxyj591y/blackhat-2012.part05.rar
http://extabit.com/file/278u4dxyj5ccm/blackhat-2012.part06.rar
http://extabit.com/file/278u4dxyiic92/blackhat-2012.part07.rar
http://extabit.com/file/278u4dxyj4zme/blackhat-2012.part08.rar
http://extabit.com/file/278u4dxyj52py/blackhat-2012.part09.rar
http://extabit.com/file/278u4dxyjrwk6/blackhat-2012.part10.rar
http://extabit.com/file/278u4dxyjqree/blackhat-2012.part11.rar
http://extabit.com/file/278u4dxyjrzqe/blackhat-2012.part12.rar
http://extabit.com/file/278u4dxyjrwh2/blackhat-2012.part13.rar
http://extabit.com/file/278u4dxyjrwg6/blackhat-2012.part14.rar
http://extabit.com/file/278u4dxyjqo7a/blackhat-2012.part15.rar
or
http://rapidgator.net/file/67241593/blackhat-2012.part01.rar.html
http://rapidgator.net/file/67244253/blackhat-2012.part02.rar.html
http://rapidgator.net/file/67245401/blackhat-2012.part03.rar.html
http://rapidgator.net/file/67245416/blackhat-2012.part04.rar.html
http://rapidgator.net/file/67245431/blackhat-2012.part05.rar.html
http://rapidgator.net/file/67245436/blackhat-2012.part06.rar.html
http://rapidgator.net/file/67245516/blackhat-2012.part07.rar.html
http://rapidgator.net/file/67245553/blackhat-2012.part08.rar.html
http://rapidgator.net/file/67239035/blackhat-2012.part09.rar.html
http://rapidgator.net/file/67239038/blackhat-2012.part10.rar.html
http://rapidgator.net/file/67240057/blackhat-2012.part11.rar.html
http://rapidgator.net/file/67240113/blackhat-2012.part12.rar.html
http://rapidgator.net/file/67240136/blackhat-2012.part13.rar.html
http://rapidgator.net/file/67240151/blackhat-2012.part14.rar.html
http://rapidgator.net/file/67238624/blackhat-2012.part15.rar.html
or
http://ryushare.com/256156e93b5a/blackhat-2012.part01.rar
http://ryushare.com/256156e93b5b/blackhat-2012.part02.rar
http://ryushare.com/256156e93b5c/blackhat-2012.part03.rar
http://ryushare.com/256156e93b5d/blackhat-2012.part04.rar
http://ryushare.com/256156e93b5e/blackhat-2012.part05.rar
http://ryushare.com/256156e93b5f/blackhat-2012.part06.rar
http://ryushare.com/273300334cda/blackhat-2012.part07.rar
http://ryushare.com/264a2b8e3c60/blackhat-2012.part08.rar
http://ryushare.com/256156e93b57/blackhat-2012.part09.rar
http://ryushare.com/264a2b8e3c61/blackhat-2012.part10.rar
http://ryushare.com/256156e93b58/blackhat-2012.part11.rar
http://ryushare.com/273300334cdc/blackhat-2012.part12.rar
http://ryushare.com/264a2b8e3c62/blackhat-2012.part13.rar
http://ryushare.com/264a2b8e3c63/blackhat-2012.part14.rar
http://ryushare.com/256156e93b59/blackhat-2012.part15.rar
Tuesday, January 8, 2013
Blackhat USA 2011: Conference Official Recordings
![Blackhat USA 2011 [2011, ENG] Blackhat USA 2011 [2011, ENG]](http://i51.fastpic.ru/big/2013/0107/98/b5b90c10c219a85def4d0904dfa51898.jpg)
Blackhat USA 2011 [2011, ENG]
English | h264, yuv420p, 1200x600, 14.98 fps | aac, 44100 Hz, mono | 16.19 GB
Genre: Video Training
English | h264, yuv420p, 1200x600, 14.98 fps | aac, 44100 Hz, mono | 16.19 GB
Genre: Video Training
The official recordings from the Blackhat USA 2011 Conference
More:http://www.securelist.com/en/blog/208193069/BlackHat_USA_2011
![Blackhat USA 2011 [2011, ENG] Blackhat USA 2011 [2011, ENG]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_v_NZaB3Ld2W3Ml42g6NyKPW_lrxuzHNpfvaoW3QjH6w7_5k33zH53eRXRTvkwndYt__lA8gxJG1qrQ2naNhW34tsviOqpizMYMxaxmuxLusAPXPW2aUrzzs6NyztPZA8BxTWtWBEr-_6bx3mLzuw=s0-d)
![Blackhat USA 2011 [2011, ENG] Blackhat USA 2011 [2011, ENG]](http://i54.fastpic.ru/big/2013/0107/a5/d0cd48f060e08abaf97c52b31e0a48a5.jpg)
Link Download
http://extabit.com/file/278u4dxyj4zom/blackhat-2011.part01.rar
http://extabit.com/file/278u4dxyiic7q/blackhat-2011.part02.rar
http://extabit.com/file/278u4dxyj52qe/blackhat-2011.part03.rar
http://extabit.com/file/278u4dxyii5zq/blackhat-2011.part04.rar
http://extabit.com/file/278u4dxyj55vq/blackhat-2011.part05.rar
http://extabit.com/file/278u4dxyj4wh2/blackhat-2011.part06.rar
http://extabit.com/file/278u4dxyj55w6/blackhat-2011.part07.rar
http://extabit.com/file/278u4dxyj4wfa/blackhat-2011.part08.rar
http://extabit.com/file/278u4dxyj592u/blackhat-2011.part09.rar
http://extabit.com/file/278u4dxyjrwli/blackhat-2011.part10.rar
http://extabit.com/file/278u4dxyjrzqu/blackhat-2011.part11.rar
http://extabit.com/file/278u4dxyjrwhi/blackhat-2011.part12.rar
http://extabit.com/file/278u4dxyjrwly/blackhat-2011.part13.rar
http://extabit.com/file/278u4dxyjrwkm/blackhat-2011.part14.rar
http://extabit.com/file/278u4dxyjrwgm/blackhat-2011.part15.rar
http://extabit.com/file/278u4dxyjqriu/blackhat-2011.part16.rar
http://extabit.com/file/278u4dxyjrwjq/blackhat-2011.part17.rar
or
http://rapidgator.net/file/67251353/blackhat-2011.part01.rar.html
http://rapidgator.net/file/67252515/blackhat-2011.part02.rar.html
http://rapidgator.net/file/67253658/blackhat-2011.part03.rar.html
http://rapidgator.net/file/67253837/blackhat-2011.part04.rar.html
http://rapidgator.net/file/67254094/blackhat-2011.part05.rar.html
http://rapidgator.net/file/67254134/blackhat-2011.part06.rar.html
http://rapidgator.net/file/67245561/blackhat-2011.part07.rar.html
http://rapidgator.net/file/67245580/blackhat-2011.part08.rar.html
http://rapidgator.net/file/67249054/blackhat-2011.part09.rar.html
http://rapidgator.net/file/67250106/blackhat-2011.part10.rar.html
http://rapidgator.net/file/67250259/blackhat-2011.part11.rar.html
http://rapidgator.net/file/67250278/blackhat-2011.part12.rar.html
http://rapidgator.net/file/67250306/blackhat-2011.part13.rar.html
http://rapidgator.net/file/67250312/blackhat-2011.part14.rar.html
http://rapidgator.net/file/67251298/blackhat-2011.part15.rar.html
http://rapidgator.net/file/67251326/blackhat-2011.part16.rar.html
http://rapidgator.net/file/67246686/blackhat-2011.part17.rar.html
or
http://ryushare.com/256156e93b65/blackhat-2011.part01.rar
http://ryushare.com/273300334ce0/blackhat-2011.part02.rar
http://ryushare.com/273300334ce1/blackhat-2011.part03.rar
http://ryushare.com/256156e93b66/blackhat-2011.part04.rar
http://ryushare.com/256156e93b67/blackhat-2011.part05.rar
http://ryushare.com/264a2b8e3c67/blackhat-2011.part06.rar
http://ryushare.com/273300334cdd/blackhat-2011.part07.rar
http://ryushare.com/264a2b8e3c64/blackhat-2011.part08.rar
http://ryushare.com/256156e93b60/blackhat-2011.part09.rar
http://ryushare.com/256156e93b61/blackhat-2011.part10.rar
http://ryushare.com/256156e93b62/blackhat-2011.part11.rar
http://ryushare.com/264a2b8e3c65/blackhat-2011.part12.rar
http://ryushare.com/273300334cde/blackhat-2011.part13.rar
http://ryushare.com/264a2b8e3c66/blackhat-2011.part14.rar
http://ryushare.com/273300334cdf/blackhat-2011.part15.rar
http://ryushare.com/256156e93b64/blackhat-2011.part16.rar
http://ryushare.com/256156e93b63/blackhat-2011.part17.rar
http://extabit.com/file/278u4dxyj4zom/blackhat-2011.part01.rar
http://extabit.com/file/278u4dxyiic7q/blackhat-2011.part02.rar
http://extabit.com/file/278u4dxyj52qe/blackhat-2011.part03.rar
http://extabit.com/file/278u4dxyii5zq/blackhat-2011.part04.rar
http://extabit.com/file/278u4dxyj55vq/blackhat-2011.part05.rar
http://extabit.com/file/278u4dxyj4wh2/blackhat-2011.part06.rar
http://extabit.com/file/278u4dxyj55w6/blackhat-2011.part07.rar
http://extabit.com/file/278u4dxyj4wfa/blackhat-2011.part08.rar
http://extabit.com/file/278u4dxyj592u/blackhat-2011.part09.rar
http://extabit.com/file/278u4dxyjrwli/blackhat-2011.part10.rar
http://extabit.com/file/278u4dxyjrzqu/blackhat-2011.part11.rar
http://extabit.com/file/278u4dxyjrwhi/blackhat-2011.part12.rar
http://extabit.com/file/278u4dxyjrwly/blackhat-2011.part13.rar
http://extabit.com/file/278u4dxyjrwkm/blackhat-2011.part14.rar
http://extabit.com/file/278u4dxyjrwgm/blackhat-2011.part15.rar
http://extabit.com/file/278u4dxyjqriu/blackhat-2011.part16.rar
http://extabit.com/file/278u4dxyjrwjq/blackhat-2011.part17.rar
or
http://rapidgator.net/file/67251353/blackhat-2011.part01.rar.html
http://rapidgator.net/file/67252515/blackhat-2011.part02.rar.html
http://rapidgator.net/file/67253658/blackhat-2011.part03.rar.html
http://rapidgator.net/file/67253837/blackhat-2011.part04.rar.html
http://rapidgator.net/file/67254094/blackhat-2011.part05.rar.html
http://rapidgator.net/file/67254134/blackhat-2011.part06.rar.html
http://rapidgator.net/file/67245561/blackhat-2011.part07.rar.html
http://rapidgator.net/file/67245580/blackhat-2011.part08.rar.html
http://rapidgator.net/file/67249054/blackhat-2011.part09.rar.html
http://rapidgator.net/file/67250106/blackhat-2011.part10.rar.html
http://rapidgator.net/file/67250259/blackhat-2011.part11.rar.html
http://rapidgator.net/file/67250278/blackhat-2011.part12.rar.html
http://rapidgator.net/file/67250306/blackhat-2011.part13.rar.html
http://rapidgator.net/file/67250312/blackhat-2011.part14.rar.html
http://rapidgator.net/file/67251298/blackhat-2011.part15.rar.html
http://rapidgator.net/file/67251326/blackhat-2011.part16.rar.html
http://rapidgator.net/file/67246686/blackhat-2011.part17.rar.html
or
http://ryushare.com/256156e93b65/blackhat-2011.part01.rar
http://ryushare.com/273300334ce0/blackhat-2011.part02.rar
http://ryushare.com/273300334ce1/blackhat-2011.part03.rar
http://ryushare.com/256156e93b66/blackhat-2011.part04.rar
http://ryushare.com/256156e93b67/blackhat-2011.part05.rar
http://ryushare.com/264a2b8e3c67/blackhat-2011.part06.rar
http://ryushare.com/273300334cdd/blackhat-2011.part07.rar
http://ryushare.com/264a2b8e3c64/blackhat-2011.part08.rar
http://ryushare.com/256156e93b60/blackhat-2011.part09.rar
http://ryushare.com/256156e93b61/blackhat-2011.part10.rar
http://ryushare.com/256156e93b62/blackhat-2011.part11.rar
http://ryushare.com/264a2b8e3c65/blackhat-2011.part12.rar
http://ryushare.com/273300334cde/blackhat-2011.part13.rar
http://ryushare.com/264a2b8e3c66/blackhat-2011.part14.rar
http://ryushare.com/273300334cdf/blackhat-2011.part15.rar
http://ryushare.com/256156e93b64/blackhat-2011.part16.rar
http://ryushare.com/256156e93b63/blackhat-2011.part17.rar
Thursday, October 18, 2012
Vivek Ramachandran, "BackTrack 5 Wireless Penetration Testing Beginner's Guide"
Vivek Ramachandran, "BackTrack 5 Wireless Penetration Testing Beginner's Guide"
English | 2011-09-09 | ISBN: 1849515581 | 220 pages | PDF | 12,7 MB
English | 2011-09-09 | ISBN: 1849515581 | 220 pages | PDF | 12,7 MB
Wireless has become ubiquitous in today’s world. The mobility and flexibility provided by it makes our lives more comfortable and productive. But this comes at a cost – Wireless technologies are inherently insecure and can be easily broken. BackTrack is a penetration testing and security auditing distribution that comes with a myriad of wireless networking tools used to simulate network attacks and detect security loopholes.
Backtrack 5 Wireless Penetration Testing Beginner’s Guide will take you through the journey of becoming a Wireless hacker. You will learn various wireless testing methodologies taught using live examples, which you will implement throughout this book. The engaging practical sessions very gradually grow in complexity giving you enough time to ramp up before you get to advanced wireless attacks.
This book will take you through the basic concepts in Wireless and creating a lab environment for your experiments to the business of different lab sessions in wireless security basics, slowly turn on the heat and move to more complicated scenarios, and finally end your journey by conducting bleeding edge wireless attacks in your lab.
There are many interesting and new things that you will learn in this book – War Driving, WLAN packet sniffing, Network Scanning, Circumventing hidden SSIDs and MAC filters, bypassing Shared Authentication, Cracking WEP and WPA/WPA2 encryption, Access Point MAC spoofing, Rogue Devices, Evil Twins, Denial of Service attacks, Viral SSIDs, Honeypot and Hotspot attacks, Caffe Latte WEP Attack, Man-in-the-Middle attacks, Evading Wireless Intrusion Prevention systems and a bunch of other cutting edge wireless attacks.
If you were ever curious about what wireless security and hacking was all about, then this book will get you started by providing you with the knowledge and practical know-how to become a wireless hacker.
Hands-on practical guide with a step-by-step approach to help you get started immediately with Wireless Penetration Testing
What you will learn from this book :
-Create a Wireless Lab for conducting experiments
-Monitor the air and sniff wireless packets
-Bypass WLAN authentication mechanism
-Crack WEP/WPA/WPA2 encryption mechanisms
-Break into a WLAN network using infrastructure flaws
-Break into a Wireless client such as a laptop
-Advanced attacks such as Man-in-the-Middle attacks and Evading WIPS
-Conduct wireless penetration test in a methodical way
This book will take you through the basic concepts in Wireless and creating a lab environment for your experiments to the business of different lab sessions in wireless security basics, slowly turn on the heat and move to more complicated scenarios, and finally end your journey by conducting bleeding edge wireless attacks in your lab.
There are many interesting and new things that you will learn in this book – War Driving, WLAN packet sniffing, Network Scanning, Circumventing hidden SSIDs and MAC filters, bypassing Shared Authentication, Cracking WEP and WPA/WPA2 encryption, Access Point MAC spoofing, Rogue Devices, Evil Twins, Denial of Service attacks, Viral SSIDs, Honeypot and Hotspot attacks, Caffe Latte WEP Attack, Man-in-the-Middle attacks, Evading Wireless Intrusion Prevention systems and a bunch of other cutting edge wireless attacks.
If you were ever curious about what wireless security and hacking was all about, then this book will get you started by providing you with the knowledge and practical know-how to become a wireless hacker.
Hands-on practical guide with a step-by-step approach to help you get started immediately with Wireless Penetration Testing
What you will learn from this book :
-Create a Wireless Lab for conducting experiments
-Monitor the air and sniff wireless packets
-Bypass WLAN authentication mechanism
-Crack WEP/WPA/WPA2 encryption mechanisms
-Break into a WLAN network using infrastructure flaws
-Break into a Wireless client such as a laptop
-Advanced attacks such as Man-in-the-Middle attacks and Evading WIPS
-Conduct wireless penetration test in a methodical way
Penetration Testing with BackTrack 4
BackTrack 4: Assuring Security by Penetration Testing
P-ckt P-blishing (April 2011) | ISBN: 1849513945 | PDF + EPUB | 392 pages | 22.1 MB
BackTrack is a penetration testing and security auditing platform with advanced tools to identify, detect, and exploit any vulnerabilities uncovered in the target network environment. Applying appropriate testing methodology with defined business objectives and a scheduled test plan will result in robust penetration testing of your network.
BackTrack 4: Assuring Security by Penetration Testing is a fully focused, structured book providing guidance on developing practical penetration testing skills by demonstrating the cutting-edge hacker tools and techniques in a coherent step-by-step strategy. It offers all the essential lab preparation and testing procedures to reflect real-world attack scenarios from your business perspective in today’s digital age.
The authors’ experience and expertise enables them to reveal the industry’s best approach for logical and systematic penetration testing.
The first and so far only book on BackTrack OS starts with lab preparation and testing procedures, explaining the basic installation and configuration set up, discussing types of penetration testing (black-box and white-box), uncovering open security testing methodologies, and proposing the BackTrack specific testing process. The authors discuss a number of security assessment tools necessary to conduct penetration testing in their respective categories (target scoping, information gathering, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, maintaining access, and reporting), following the formal testing methodology. Each of these tools is illustrated with real-world examples to highlight their practical usage and proven configuration techniques. The authors also provide extra weaponry treasures and cite key resources that may be crucial to any professional penetration tester.
This book serves as a single professional, practical, and expert guide to developing hardcore penetration testing skills from scratch. You will be trained to make the best use of BackTrack OS either in a commercial environment or an experimental test bed.
A tactical example-driven guide for mastering the penetration testing skills with BackTrack to identify, detect, and exploit vulnerabilities at your digital doorstep.
What you will learn from this book :
Initiate the BackTrack OS environment in your test lab by installing, configuring, running, and updating its core system components
Draw a formal BackTrack testing methodology
Scope your target with definitive test requirements, limitations, and business objectives, and schedule the test plan
Gain practical experience with a number of security tools from BackTrack logically divided into sub-categories of testing methodology
Practice the process of reconnaissance, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, and maintaining access to your target for evaluation purposes
Document, report, and present your verified test results to the relevant authorities in a formal reporting structure
Assess the various technologies comprising your target information system’s environment, such as web applications, network administration servers, workstations, Cisco devices, firewalls, load balancers, routers, switches, intrusion detection and prevention devices, and many more
Examine and research the vulnerability in greater detail before attempting to exploit it by taking control of the target, thus reducing any false positives
Exploit human vulnerability by wrapping yourself with the art of deception to acquire the target
Approach
Written as an interactive tutorial, this book covers the core of BackTrack with real-world examples and step-by-step instructions to provide professional guidelines and recommendations to you. The book is designed in a simple and intuitive manner, which allows you to explore the whole BackTrack testing process or study parts of it individually.
Who this book is written for
If you are an IT security professional or network administrator who has a basic knowledge of Unix/Linux operating systems including awareness of information security factors, and you want to use BackTrack for penetration testing, then this book is for you.
Download Rapidgator.net
http://rapidgator.net/file/36794691/Packtpub.BackTrack.4.Apr.2011.rar.html
Download Letitbit.net
http://letitbit.net/download/04351.0b0e2cb964d3c4fb1b6ad2b16734/Packtpub.BackTrack.4.Apr.2011.rar.html
Download Lumfile.com
http://lumfile.com/txeenca0mbpu/Packtpub.BackTrack.4.Apr.2011.rar.html
The authors’ experience and expertise enables them to reveal the industry’s best approach for logical and systematic penetration testing.
The first and so far only book on BackTrack OS starts with lab preparation and testing procedures, explaining the basic installation and configuration set up, discussing types of penetration testing (black-box and white-box), uncovering open security testing methodologies, and proposing the BackTrack specific testing process. The authors discuss a number of security assessment tools necessary to conduct penetration testing in their respective categories (target scoping, information gathering, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, maintaining access, and reporting), following the formal testing methodology. Each of these tools is illustrated with real-world examples to highlight their practical usage and proven configuration techniques. The authors also provide extra weaponry treasures and cite key resources that may be crucial to any professional penetration tester.
This book serves as a single professional, practical, and expert guide to developing hardcore penetration testing skills from scratch. You will be trained to make the best use of BackTrack OS either in a commercial environment or an experimental test bed.
A tactical example-driven guide for mastering the penetration testing skills with BackTrack to identify, detect, and exploit vulnerabilities at your digital doorstep.
What you will learn from this book :
Initiate the BackTrack OS environment in your test lab by installing, configuring, running, and updating its core system components
Draw a formal BackTrack testing methodology
Scope your target with definitive test requirements, limitations, and business objectives, and schedule the test plan
Gain practical experience with a number of security tools from BackTrack logically divided into sub-categories of testing methodology
Practice the process of reconnaissance, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, and maintaining access to your target for evaluation purposes
Document, report, and present your verified test results to the relevant authorities in a formal reporting structure
Assess the various technologies comprising your target information system’s environment, such as web applications, network administration servers, workstations, Cisco devices, firewalls, load balancers, routers, switches, intrusion detection and prevention devices, and many more
Examine and research the vulnerability in greater detail before attempting to exploit it by taking control of the target, thus reducing any false positives
Exploit human vulnerability by wrapping yourself with the art of deception to acquire the target
Approach
Written as an interactive tutorial, this book covers the core of BackTrack with real-world examples and step-by-step instructions to provide professional guidelines and recommendations to you. The book is designed in a simple and intuitive manner, which allows you to explore the whole BackTrack testing process or study parts of it individually.
Who this book is written for
If you are an IT security professional or network administrator who has a basic knowledge of Unix/Linux operating systems including awareness of information security factors, and you want to use BackTrack for penetration testing, then this book is for you.
Download Rapidgator.net
http://rapidgator.net/file/36794691/Packtpub.BackTrack.4.Apr.2011.rar.html
Download Letitbit.net
http://letitbit.net/download/04351.0b0e2cb964d3c4fb1b6ad2b16734/Packtpub.BackTrack.4.Apr.2011.rar.html
Download Lumfile.com
http://lumfile.com/txeenca0mbpu/Packtpub.BackTrack.4.Apr.2011.rar.html
Tuesday, September 18, 2012
Career in Penetration Testing: What Would a Penetration Tester Do?
IT, cyber, and network security are huge fields in today’s world. As more and more information becomes available and is stored online, there becomes a bigger need than ever before for security of that information. The world needs highly skilled individuals that can protect the infrastructure of networks and systems.
What Would a Penetration Tester Do?
The job of a penetration tester is to find exploits, weak points, or holes in computer systems and software. This would include trying to break into a system in order to find out where the vulnerabilities are. Running a number of tests is required in order to do this. Running these tests and filling out assessments and reports of is a very important aspect of the job. This allows pen testers to report what they have discovered so that any issues can be resolved.
Pen testers do get to use their imagination and creativity when coming up with their own tests to run on systems. Sometimes pre-determined tests will be run, but a lot of the time it will be required to come up with and run custom ones. This does allow the pen tester to get creative and have a little fun when coming up with tests, but also requires skill and technical knowledge to implement.
A penetration tester does hold a significant amount of responsibility. It is their job to run formal tests on web-based applications, networks, or any other computer systems. The security of servers, networks, and systems lies in the hands of the penetration tester. Areas of specialty include wireless networks, databases, software, company websites, and more. Pen testers may be required to work in multiple areas, but may also specialize in just one single area.
What Would a Penetration Tester Do?
The job of a penetration tester is to find exploits, weak points, or holes in computer systems and software. This would include trying to break into a system in order to find out where the vulnerabilities are. Running a number of tests is required in order to do this. Running these tests and filling out assessments and reports of is a very important aspect of the job. This allows pen testers to report what they have discovered so that any issues can be resolved.
Pen testers do get to use their imagination and creativity when coming up with their own tests to run on systems. Sometimes pre-determined tests will be run, but a lot of the time it will be required to come up with and run custom ones. This does allow the pen tester to get creative and have a little fun when coming up with tests, but also requires skill and technical knowledge to implement.
A penetration tester does hold a significant amount of responsibility. It is their job to run formal tests on web-based applications, networks, or any other computer systems. The security of servers, networks, and systems lies in the hands of the penetration tester. Areas of specialty include wireless networks, databases, software, company websites, and more. Pen testers may be required to work in multiple areas, but may also specialize in just one single area.
Career and Salary
All this responsibility that a pen tester holds does not come without reward. Salaries for IT consultants range from about $55,000 - $88,000 per year. Entry level will be closer to the lower end of the salary of course, but there are plenty of opportunities for advancement. Demand is good for IT consultants with skills in penetration testing. Working in government positions offers a slightly lower salary range of about $52,000 - $87,000 per year. With demand in both the private and public sectors, job outlook seems good for individuals interested in penetration testing.
Technology is constantly becoming a bigger and bigger part of society and demand for security of online information is only increasing.
All this responsibility that a pen tester holds does not come without reward. Salaries for IT consultants range from about $55,000 - $88,000 per year. Entry level will be closer to the lower end of the salary of course, but there are plenty of opportunities for advancement. Demand is good for IT consultants with skills in penetration testing. Working in government positions offers a slightly lower salary range of about $52,000 - $87,000 per year. With demand in both the private and public sectors, job outlook seems good for individuals interested in penetration testing.
Technology is constantly becoming a bigger and bigger part of society and demand for security of online information is only increasing.
Want to learn more about careers in penetration testing? Visit the TrainACE penetration testing class for more info. TrainACE also provides IT security classes in many other areas such as CEH, CHFI, cloud security, and more. Visit the main information security page here.
Guest post by Alan Rosinski
Guest post by Alan Rosinski
Monday, April 30, 2012
Learn How to Scan all open TCP and UDP ports using VISION
Vision, a host based Forensic Utility is the GUI successor to the well-known freeware tool, Fport. This innovative new product from Foundstone shows all of the open TCP and UDP ports on a machine, displays the service that is active on each port, and maps the ports to their respective applications. Vision allows users to access a large amount of supplementary information that is useful for determining host status by displaying detailed system information, applications running, as well as processes and ports in use.
Key Features
- Interrogate ports and identify potential "Trojan" services by using the "Port Probe" command in the port mapper. Using "Port Probe", Vision will enable you to send a customized string of information to the port. Based on the response from the port, a determination can be made to either kill the port, using the "Kill" command, or leave it as is.
- View system events by sorting by application, process, service, port, remote IP, and device drivers in ascending or descending order.
- Identify and review detailed information about Services and Devices to determine if they are Running or Stopped.
List Applications Running
List Services Running

List Devices Running


Faq
Q. Will Vision work on Windows 9x, Me, or XP?
A. Vision will not work on Windows 9x, or Me. It will work with Windows XP.
Q. I get “Must be Admin” error when trying to launch. I am the Administrator, so what’s the problem?
A. Check to ensure that nbt binding is enabled. In NT 4 this is done in your network interface bindings. Under Win2k check to ensure that you have the TCP/IP Netbios helper enabled.
System Requirements
- NT 4/ Win 2000
- NT 4 needs psapi.dll
- 800x600 res. minimum
- 256 colors min
- 32MB
SOURCE: http://www.foundstone.com
Sunday, April 29, 2012
Simple security audit & Penetration test tool HackBar 1.4.2 download for free: Its Add-ons for Firefox
Version 1.4.2
Works with Firefox: 1.5 – 3.6.*
Updated May 13, 2009
Developer Johan Adriaans
Rating Rated 5 out of 5 stars
# In general
This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site. Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster. If you want to learn to find security holes, you can also use this toolbar, but you will probably also need a book, and a lot of google :)
# The advantages are:
- Even the most complicated urls will be readable
- The focus will stay on the textarea, so after executing the url (ctrl+enter) you can just go on typing / testing
- The url in textarea is not affected by redirects.
- I tend to use it as a notepad :)
- Useful tools like on the fly uu/url decoding etc.
- All functions work on the currently selected text.
# Load url ( alt a )
This loads the url of the current page into the textarea.
# Split url ( alt s )
When this button is clicked, the url/text in the textarea will be split into multiple lines using the ? and & character
# Execute ( alt x, ctrl enter )
This will execute the current url in the textarea, i mostly use ctrl+enter
# INT -1 ( alt - )
First select a number in the textarea and press this button, the number will be lowered by 1 and the url will be loaded.
# INT +1 ( alt + )
Again first select a number in the textarea and press this button, 1 will be added to the number and the url will be loaded.
# HEX -1 ( control alt - )
First select a number in the textarea and press this button, the number will be lowered by 1 and the url will be loaded.
# HEX +1 ( control alt + )
Again first select a number in the textarea and press this button, 1 will be added to the number and the url will be loaded.
# MD5 Hash ( alt m )
this is a standard hashing method, often used as an encryption method for passwords. It will MD5 hash the currently selected string.
# SHA-1/256
this is a standard hashing method, often used as an encryption method for passwords. It will SHA-1/256 hash the currently selected string.
# MySQL CHAR() ( alt y )
If quotes are escaped but you did find an SQL injection thats exploitable, you can use this button to convert lets say:
load_file('/etc/passwd') --> load_file(CHAR(47, 101, 116, 99, 47, 112, 97, 115, 115, 119, 100))
Thus omiting the use of quotes to load a file.
You can also use this on
WHERE foo LIKE ('%bar%') --> WHERE foo LIKE (CHAR(37, 98, 97, 114, 37))
# MsSQL CHAR() ( alt q )
Same story as MySQL CHAR(), MsSQL has a slightly different CHAR syntax
--> WHERE foo LIKE ( CHAR(37) + CHAR(98) + CHAR(97) + CHAR(114) + CHAR(37))
# Base64 encode / decode
Base64 encoding ( UU ) is often used to store data (like a return url etc.) This will help you to read those values.
# URLencode / decode
This will encode or decode the currently selected characters to url safe characters. I mostly use it to end a query with # (%23) when in a pseudo path where i cant use /* or --
And lots more ;) Go test it!
Saturday, April 28, 2012
Learn How to Scan open ports using Angry IP Scanner
From the Angry IP scanner software enter the target IP address.


Once the scan has completed a window will appear identifying the results. Click OK.
In this example:
- Port 21 (FTP [File Transfer Protocol]) is open.
- Port 80 (Web) is open.
- Port 139 (Windows Share) is open.
- Port 445 (Windows Share) is open.
 Right-click on the IP address to bring up a menu; then select OPEN COMPUTER, then IN EXPLORER.
Right-click on the IP address to bring up a menu; then select OPEN COMPUTER, then IN EXPLORER.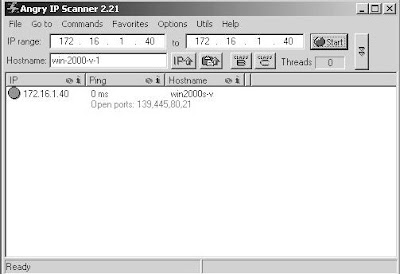
In this example, the results revealed the following:
- The Database directory is shared.
- The Downloads directory is shared.
- The Personal directory is shared.
- There may be Printers shared on the target.
- The Windows scheduler is running and may have tasks that can be modified.
 If the shares ask you for a username/password when attempting to access them, initiate a NULL session and try again.
If the shares ask you for a username/password when attempting to access them, initiate a NULL session and try again.Tuesday, February 14, 2012
Backtrack 4 Download for Windows VMWare & Torrents

BackTrack is a live CD Linux distribution that focuses on penetration testing. A merger of two older security-related distros — Whax and Auditor Security Collection — BackTrack bundles more than 300 security tools.
BackTrack is based on the SLAX distribution (a live CD derived from Slackware) and runs a patched 2.6.20 kernel. It offers users both KDE and Fluxbox desktop environments.
To start using BackTrack, download the ISO image and burn it to a CD. Insert the disc and boot your machine. Once booted, the system start at runlevel 3 (text mode), where you must log in as root and choose whether to start KDE or Fluxbox or just use the terminal.
BackTrack provides clear, concise instructions for logging in, starting the window manager, and configuring the video card before you see the login prompt. If you’ve never used BackTrack before, use a graphical environment, since it will help you understand how all the included applications are organized and let you take advantage of some graphical utilities. When the window manager comes up you’ll find some ordinary desktop programs, such as Firefox, Gaim, K3b, and XMMS, within a nice environment with beautiful wallpaper and window transparency.
Don’t let the attractive appearance fool you — BackTrack packs a punch. The security tools are arranged inside a Backtrack submenu. This is a big improvement over older releases, because you can easily follow an attack methodology: starting by collecting information and end by hiding your actions.
The tools are arranged in 12 categories, such as vulnerability identification, penetration, privilege escalation, radio network analysis, and reverse engineering. Among the more than 300 security tools you’ll find such familiar names as the Metasploit Framework, Kismet, Nmap, Ettercap, and Wireshark (previously known as Ethereal).
One of the core points of this release is the attention to detail. For example, when you choose most of the programs from the Backtrack menu, a console window opens with the output of the program’s help. Some tools have been bundled with scripts that in a few steps configure and run the program for you. For example, if you run the Snort intrusion detection application, a script asks for some passwords and then sets up MySQL, Apache, Base, and Snort itself so you can easy browse alert logs via a Web browser.
If you open Firefox or Konqueror you’ll find some useful security-oriented bookmarks. In the Documents submenu the developers have included PDF manuals for the ISSAF and OSSTMM security methodologies. There are also some tools that you wouldn’t expect inside a live CD; for example, you have a popular debugger for Windows, OllyDbg, which runs fine through Wine, so you can even debug .exe files.
If you like the live CD, you can install BackTrack to a hard drive (decompressed, it requires 2.7GB of space) or USB memory stick (compressed, 700MB) using a graphical wizard.
While BackTrack is an excellent tool, nothing is perfect. Unfortunately it doesn’t include Nessus, the popular security scanner, due to license problems. I tried to start PostgreSQL from the Services menu, but it gave an error. And it seems as if the developers forgot to update the Backtrack menu in Fluxbox, because it offers the previous version arrangement. Tools like VMware and Nessus appear on the menu but are broken links because they have been removed from this release.
Despite a few little bugs and problems, BackTrack is the best distribution I’ve found for handling security-oriented tasks out of the box.
Download Links :
Last Update: 11.01.2010
Description: Image Download
Name:: bt4-final.iso
Size: 1570 MB
MD5: af139d2a085978618dc53cabc67b9269
Description: VM Image Download
Name:: bt4-final-vm.zip
Size: 2000 MB
MD5: 733b47fad1d56d31bc63c16b3706a11c
FOR OLDER VERSIONS CLICK HERE
To learn HOW TO USE BACKTRACK & for all BACKTRACK TUTORIALS & COMMANDS: CLICK HERE & JOIN THIS FORUM
Monday, February 13, 2012
Hack Using NESSUS & METASPLOIT | Step by Step User Guide
How to Hack Website | How to Hack Web Server | Step by Step Hacking Video Tutorial | Hack Using NESSUS & METASPLOIT | Step by Step User Guide
In Depth Security Assessment With a Full Report Detailing Vulnerabilities Discovered Using NESSUS & OpenVas: Learn how to Hack a Website & Webserver
Hi Readers, continuing to my posts The best vulnerability scanner software and assessment tool: Nessus & The Best Penetration Testing and Vulnerability Exploitation Tool: Metasploit Framework
Yesterday I have posted an article regarding how to hack an password. That post was for kidies who take hacking as a fun. Now today this post is for advance readers. Here I am going to share some real hacking techniques using which one can hack any server or website. This post is for educational purpose only.
NOTE: No scans will be initiated against any systems/server until the outline of the system/server owner assessment plan is confirmed as acceptable to owner.
Tools Used during penetration testing are freely available on internet:
- NESSUS
- OpenVAS Server
- OpenVAS Client
- Nmap
- Nikto
- SQLix download here or here
- SQLMap
- Metasploit
Steps need to be followed to hack a server is as cited below:
- Do a manual review of the target system or server to get an overview of the target. This is phase-1 and known as Reconnaissance.
- Second step is Service enumeration. Here you have to use Nmap to determine what services are open and available for manual testing. This is phase-2 and known as Scanning. To know how to perform Enumeration and footprinting attack, visit this link.
- The third step is Scanning target to find the vulnerabilities. This is also part of phase-2 Scanning. For this you have to use NESSUS or OPEN VAS. These tools will scan all open ports, regardless of common and defaulted settings. This will confirm listening services and check those against a database of exploitable services. To see if you are running any services that are mis-configured or vulnerable to exploits. To know how NESSUS works visit this link. If you want to working of NESSUS...OR How to use NESSUS visit this link. To visit NESSUS video tutorials available on internet visit this link.
- You can also use Nikto. It will used to check the web server(s) for mis-configurations and exploitable web applications. To know how Nikto works visit this link.
- After all these scanning, play with SQL. Use SQLiX and Sqlmap for this. You can also use few more SQL tools, softwares and techniques. To know these underground SQL tips n tricks visit this link & This Link
- The next step is to get access on system using the vulnerabilities found. This is phase-3 known as Gaining Access on remote system. This you can achieve using Metasploit software. To know how to use metasploit, visit this link. Here you will all the available video tutorial for metasploit. A very good to start. Using these videos you can easily learn how to use metasploit. The most up to date video for Metasploit 3 can be found here: Exploring Metasploit 3 and the New and Improved Web Interface – Part 1 & Exploring Metasploit 3 and the New and Improved Web Interface – Part 2. A good flash tutorial that shows you step by step how to use it: Metasploit at Iron Geek. There’s a presentation by HD Moore himself at Cansecwest 2006: csw06-moore.pdf And a couple of videos spawned from that here: Computer defense – TASK Presentation
- The next step is to maintain you access on the compromised system. This is phase-4 and known as Maintaining Access.
- THIS IS THE MOST IMPORTANT STEP AND THE LAST PHASE. This is phase-5 known as Covering Tracks. After you activities, you must remove all your track records....;) othet wise you know...IT act is very strong.
This tutorial is designed to provide you with recommendations for securing your server against the majority of attackers. Below are some sample reports showing Nessus and OpenVas. It is recommended that always run multiple scanning tools. Never rely on a single automated scanning. Automated scanners miss a lot and are prone to false positives.
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Sample Report
Please report any problem OR broken link to us on amarjit@freehacking.net. You can also leave a comment here.
Saturday, February 4, 2012
Local File Inclusion Vulnerability Scanner version 1.0 released
Local File Inclusion Vulnerability Scanner version 1.0 released by Valentin
Description
The Simple Local File Inclusion Vulnerability Scanner helps you to find LFI vulnerabilities.
Usage
./lfi_scanner.py –url=
Usage example
./lfi_scanner.py –url=”http://www.example.com/page.php?file=main”
Usage notes
- Always use http://….
- This tool does not work with SEO URLs, such as http://www.example.com/news-about-the-internet/.
- If you only have a SEO URL, try to find out the real URL which contents parameters.
Feature list
- Provides a random user agent for the connection.
- Checks if a connection to the target can be established.
- Tries to catch most errors with error handling.
- Contains a LFI vulnerability scanner.
- Finds out how a possible LFI vulnerability can be exploited (e.g. directory depth).
- Supports nullbytes!
- Supports common *nix targets, but no Windows systems.
Known issues
- This tool is only able to handle “simple” LFI vulnerabilities, but not complex ones.
- Like most other LFI scanners, this tool here also has trouble with handling certain server responses.
Some notes
- Tested with Python 2.6.5.
- Modify, distribute, share and copy the code in any way you like!
- Please note that this tool was created for educational purposes only.
- Do not use this tool in an illegal way. Know and respect your local laws.
- Only use this tool for legal purposes, such as pentesting your own website
- I am not responsible if you cause any damage or break the law.
- Power to teh c0ws!
Friday, February 3, 2012
Joomla RFI Remote File Inclusions Attack | Joomla LFI Local File Inclusions Attack
Joomla LFI Local File Inclusions Attack | Joomla RFI Remote File Inclusions Attack
By Valentin
Examples for Joomla local file inclusions
Local file inclusions are very funny. You tell the website what you want to see. Awesome! You want to view the configuration file which contains the database login credentials? No problem.
You want to view the /etc/passwd file if Joomla is hosted on a Linux box? You can do that.
Local file inclusions are also a common problem in Joomla extensions. Many of them are vulnerable for this type of attack and some of them never get fixed. This may lead to a server hack, which is not funny any more - at least for the system administrator.
A typical URL being vulnerable to LFI looks like this:
index.php?option=com_blablubb&Item=2&view=guestbookpage
Typically most of the vulnerable parameters are this one:
- controller
- view
- layout
- page
To give you some proper understanding of typical affected
URLs I provide you with some examples I found earlier this year:
URL: index.php?option=com_jejob&view=some_value
Vulnerable Parameter: view
URL: index.php?option=com_jeajaxeventcalendar&view=some_value
Vulnerable Parameter: view
URL: index.php?option=com_jradio&controller=some_value
Vulnerable Parameter: controller
((I didn't find this one.))
Now let's see how we can use this:
index.php?option=com_jradio&controller=../../../../etc/passwd
In this case we need to use the famous Nullbyte which helps us to bypass a restriction which is set in the responsible PHP script of the component.
In the example above the controller parameter is used to include a file from the local hard disk. This file contains useful information for us.
If you are not familiar with local file inclusions I recommend you look a tutorial up since I will not explain any details here.
Now with the knowledge about a LFI vulnerability within a Joomla component, we can try to access the configuration.php of Joomla. This file contains very very interesting information.
Since many LFIs also reveal PHP source code, we try this one:
index.php?option=com_blabla&view=../../../configuration.php
The source code of the file is shown and we receive the login data for the current database user. Now find a PHPMyAdmin login on the same server and try to login with this data.
You now have access to all Joomla tables and can basically do what you want.
Examples for Joomla remote file inclusions
A typical RFI URL looks like a LFI URL. In order to give you a better feeling of how to see a RFI vulner-ability within seconds, I show you some examples
URL: index.php?option=com_sef&Itemid=&mosConfig.absolute.path=.
Vulnerable Parameter: &mosConfig.absolute.path
URL: index.php?option=com_jomestate&task=.
Vulnerable Parameter: task
When you found a RFI vulnerability, try to include your PHP shell which is hosted on another box. Once you uploaded it, you are able to browse all Joomla files and download them, change them, remove them...
No Joomla installation is safe when there is an exploited RFI.
Thursday, February 2, 2012
Joomla Hacking Tools: Hack Joomla with self-written tools by Valentin

Joomla Hacking Tools: Hack Joomla with self-written tools by Valentin
#1
Joomla QPersonel Exploit
http://www.xenuser.org/exploits/joomla_com_qpersonel_sploit.py
#2
Automated Joomla SQL Injection Exploiter
http://www.xenuser.org/exploits/joomla_sqli_sploiter.py
#3
Joomla BF Quiz Exploit
http://www.xenuser.org/exploits/joomla_com_bfquiz_sploit.py
#4
Column Fuzzer
http://xenuser.org/tools/column_finder.py
#5
Simple SQL Injection Vulnerability Scanner
http://www.xenuser.org/tools/sqli_scanner.py
#6
Simple Log File Analyzer
http://www.xenuser.org/tools/scan_log.py
#7
Simple Local File Inclusion Exploiter
http://www.xenuser.org/tools/lfi_sploiter.py
These tools can help you to exploit vulnerabilities within Joomla or some extensions.
NOTE: Read the help (included in those tools) for details.
The Simple Log File Analyzer could be used for scanning your Apache log files. It shows if there are hack attempts.
Subscribe to:
Comments (Atom)

