Wednesday, April 30, 2014
Fool the Network Hunters (Hackers)
Wednesday, July 3, 2013
Zarp - Network Attack Framework: Local Network Attack Tool
Functionality:
- Poisoners
- Parameter
- Services
- Sessions
- Scanners
- DoS Attacks
- Sniffers
Download: https://github.com/hatRiot/zarp
https://defense.ballastsecurity.net/wiki/index.php/Zarp
Sunday, June 30, 2013
SpiderFoot: Free open-source footprinting tool
Grab it from: http://www.spiderfoot.net/
- Scans are even more configurable than before
- All scan data stored locally in an SQLite database for querying, reporting and analysis - Many more scans/tests included (GeoIP, URL linkage, web technology, port scans...) - You can now easily extend functionality by writing your own modules in Python
- Completely new user interface, which is now entirely web-based
- Configuration state is stored between runs
- Scanning can be remotely controlled
Monday, April 1, 2013
Cisco Type 4 Passwords cracked–Coding mistake endangers devices

There are two options to generate a Type 5 password:
- Using another device running a Cisco IOS or Cisco IOS XE release without Type 4 support
- Using the openssl command-line tool (part of the OpenSSL Project)
Wednesday, March 20, 2013
Is MPLS Network Really Secure? MPLS truth revealed against security.
The truth is that MPLS offers-
• No protection against misconfiguration - Human and machine errors as well as OS bugs can result in MPLS traffic being misrouted.
• No protection from attacks within the core - MPLS is vulnerable to all the traditional WAN attack vectors.
• No protection or detection of sniffing/snooping - It is impossible to detect if someone is siphoning or replicating data - there is no “alarm” that goes off if data is being stolen.
• No Data Security - The data is left in the clear and can be accessed, replicated, or used by anyone who gains access to it.
• Traffic Class (TC) bits are used to provide services such traffic prioritization.
• The Stacking bit (S) allows multiple labels to be used.
• TTL is a “time to live” marker to allow packets to expire.
Hackers know: The mechanism used to separate traffic can also be used to identify targets of interest!
Hackers know: Provisioning and management are to data security what traffic lights are to bank robbers - they do not prevent data theft!
Hackers know: Traffic is not accidentally leaking out to the Internet, it is being stolen right off the MPLS backbone!
Hackers know: Post-event notification is not a substitute for prevention!
Why You Need to Measure Delay, Jitter and Packet Loss on Data Networks

To meet today’s business priorities and ensure user satisfaction and usage, IT groups and service providers are moving toward availability and performance commitments by IP application service levels or IP service-level agreements (SLAs).
Prior to deploying an IP service, network managers must first determine how well the network is working, second, deploy the service, such as voice over IP (VoIP), and finally, verify that the service levels are working correctly—which is required to optimize the service deployment. IP SLAs can help meet life-cycle requirements for managing IP services. To ensure the successful implementation of VoIP applications, you first need to understand current traffic characteristics of the network. Measuring jitter, delay, and packet loss and verifying classes of
service (CoS) before deployment of new applications can aid in the correct redesign and configuration of traffic prioritization and buffering parameters in data network equipment.
Delay is the time it takes voice to travel from one point to another in the network. You can measure delay in one direction or round trip. One-way delay calculations require added infrastructure such as Network Time Protocol (NTP) and clock synchronization and reference clocks. NTP is deployed to synchronize router clocks and also when global positioning system (GPS) or another trusted reference time is needed in the network. Accuracy of clocks and clock drift affect the accuracy of one-way delay measurements. VoIP can typically tolerate delays of up to approximately 150 ms one way before the quality of a call is unacceptable to most users.
Jitter is the variation in delay over time from point to point. If the delay of transmissions varies too widely in a VoIP call, the call quality is greatly degraded. The
amount of jitter that is tolerable on the network is affected by the depth of jitter buffer on the network equipment in the voice path. When more jitter buffer is available, the network is more able to reduce the effects of the jitter for the benefit of users, but a buffer that is too big increases the overall gap between two packets. One-way jitter measurement is possible and does not require clock synchronization between the measurement routers.

Packet loss severely degrades voice applications and occurs when packets along the data path are lost. Measuring Network Performance Key capabilities in the Cisco IOS Software can help
you determine baseline values for VoIP application performance on the data network. The ability to gather data in real time and on demand makes it feasible for IT groups and service providers to create or verify SLAs for IP applications; baseline values can then be used to substantiate an IP SLA for VoIP.
Cisco IOS Service Assurance Agent (SAA) technology is a component of an IP SLA solution and the Round Trip Time Monitor (RTTMON) MIB, which enable the testing and collection of delay, jitter, and packet loss measurement statistics. Active monitoring with traffic generation is used for edge-to-edge measurements in the network to monitor the network
performance. You can use the CiscoWorks Internetwork Performance Monitor (IPM) network management
Is Your Network Ready for Voice?
Measuring Delay, Jitter, and Packet Loss for Voice-Enabled Data Networks Your success or failure in deploying new voice technologies will depend greatly on your ability to understand the traffic characteristics of the network and then applying your knowledge to engineer the appropriate network configurations to control those characteristics.
Application or the IOS command-line interface (CLI) to configure and retrieve data from the RTTMON MIB, or choose from a wide selection of Cisco ecosystem partners and public domain software to configure and retrieve the data. In addition, the CiscoWorks IPM features are now also available in the WAN Performance Utility (WPU) module of CiscoWorks IP Telephony Environment Monitor (ITEM) network management software.
Deploying Delay/Jitter Agent Routers
You can measure delay, jitter, and packet loss by deploying almost any Cisco IOS device, from a
Cisco 800 Series Router on up. Two deployment scenarios are possible: You can either purchase dedicated routers for SLA measurements or use current routers within the network. Place the routers in a campus network along with hosts to provide statistics for end-to-end connections.
It is not practical to measure every possible voice path in the network, so place the dedicated routers in typical host locations to provide a statistical sampling of typical voice paths.
In the case of VoIP deployments using traditional phones connected to Cisco routers using FXS station ports, the router to which the phones are connected also serves as the delay/jitter measurement device. Once deployed, the operation collects statistics and populates Simple Network Management Protocol (SNMP) MIB tables in the probe router. You can then access the data either through the CiscoWorks IPM, or through simple SNMP polling tools and other third-party applications. Additionally, after baseline values have been established, you can configure operations to send alerts to a network management system (NMS) station if thresholds
for delay, jitter, and packet loss are exceeded.
Simulating a Voice Call
One of the strengths of using Cisco IOS SAA as the testing mechanism is that you can simulate a voice call. In Cisco IOS Software Release 12.3(4)T and later, you can configure the VoIP codec directly in the CLI and simulate a voice call. This release also includes voice quality estimates, Mean Opinion Scores (MOS), and Planning Impairment Factor (PIF) scores. Earlier versions of the Cisco IOS Software enable you to estimate a VoIP codec using the correct packet size, spacing, and interval for the measurement data and enter the appropriate parameters.
The CoS can be set on data or VoIP tests, which allows you to verify how well QoS is working in the network. Examples of how to simulate a voice call are shown below.
type jitter dest-ipaddr 10.1.1.2 dest-port 14384 codec g711alaw
rtr schedule 1 start-time now
With earlier IOS releases before 12.3(4)T you can use the rtp/udp even port numbers in the range of 16384 to 32766. The user then approximates 64 kbit/s, and the packet size is 200 bytes {(160 bytes of payload + 40 bytes for IP/UDP/RTP (uncompressed) }. You can simulate that type of traffic by setting up the jitter operation as shown below.
- Send the request to rtp/udp port number 14384
- Send 172 byte packets (160 payload + 12 byte RTP header size) + 28 bytes (IP + UDP)
- Send 3000 packets for each frequency cycle
- Send every packet 20 milliseconds apart for a duration of 60 seconds and sleep 10 seconds before starting the next frequency cycle
((3000 datagrams * 160 bytes per datagram)/ 60 seconds))* 8 bits per byte = 64 kbit/s
The configuration on the router would look like this:
type jitter dest-ipaddr 10.1.1.2 dest-port 14384 numpackets 3000 request-data-size 172**
frequency 70
rtr schedule 1 start-time now
Note that IP+UDP is not considered in the requestdata-size, because the router internally adds them to the size automatically.
Delay/Jitter Probe Deployment Example
router1# rtr responder rtr 1 type jitter dest-ipaddr 10.1.2.1 dest-port 14384 codec g711alaw
tos 160 frequency 60 rtr schedule 1 start-time now
tos 160 frequency 60 rtr schedule 1 start-time now
Monitoring Thresholds
You can use the CLI, CiscoWorks IPM, or the WPU in CiscoWorks ITEM to configure features and monitor data. You can use this data to manage IP SLAs that have been created for VoIP. After you have determined baseline values, you can reconfigure the jitter operations to monitor the network. When predetermined delay and jitter service-level thresholds are reached or exceeded, NMS stations will be alerted.
The Cisco IOS SAA threshold command sets the rising threshold (hysteresis) that generates a reaction event and stores history information for the operation. Cisco IOS SAA can measure and create thresholds for round-trip time delay, average jitter, connectivity loss, one-way packet loss, jitter, and delay.
Sample Service Assurance Threshold Configuration
Understanding the traffic characteristics of the network before you deploy new advanced applications is the key to successful implementations. Delay, jitter, and packet loss greatly affect VoIP applications. Your success or failure in deploying new voice technologies will depend greatly on your ability to understand the traffic characteristics of the network and then applying your knowledge to engineer the appropriate network configurations to control
those characteristics.
Tuesday, March 19, 2013
Interview questions for fresher network engineer: Tips and Tricks for CCNA, CCNP, OSPF, BGP, MPLS-VPN | Ask all your queries online absolutely free
Wednesday, January 2, 2013
OSPF Vs EIGRP : Which Routing Protocol To Select?
1. Between OSPF and EIGRP which one is the best to deploy and why?
2. Which protocol converges faster and highly available?
3. Which protocol uses fewer resources?
4. Which protocol is easier to deploy and operate?
5. Which protocol is easier to understand and configure?
6. Which protocol is easier to scale in large network?
7. Which protocol is more scalable and easy to adopt changes?
Every protocol has its own merits and de-merits. Between OSPF which is a link state routing protocol in its own area and becomes a distance vector routing protocol from one area to another and EIGRP is a distance vector routing protocol, In fact, its not a pure DV routing protocol.
Convergence speed depends on the number of routers and routes involved in the network. The more the number, less the convergence time. Convergence speed depends on various attributes defined in Fast Convergence Tools.
At broader level below are few points which can be used as high level to understand the protocol at its best:-
1. EIGRP uses metric based on bandwidth, delay, reliability, load and MTU whereas OSPF uses interface cost which is inversely proportional to bandwidth. EIGRP is considered as best in terms of selecting the path on different attributes.
2. EIGRP is proprietary to CISCO whereas OSPF is based on OPEN Standard.
3. EIGRP sends hop by hop query when feasible successor is not found whereas OSPF syncs its LSA(LSA1, LSA2, LSA3, LSA4 and LSA5) database whenever there is change in network topology. EIGRP is considered as best as it minimizes the routing information.
4. EIGRP is simpler to understand whereas OSPF has lot of things to understand. It depends how comfort you are to select out of these.
5. EIGRP does automatic summarization whereas OSPF doesn’t.
6. EIGRP does support both equal and unequal cost load sharing whereas OSPF doesn’t.
7. EIGRP limits the usage by 50% of the link bandwidth whereas OSPF does 100%.
8. EIGRP is faster to converge when it has feasible successor but OSPF doesn’t. Still there are lot of tools available to make OSPF better in terms of convergence.
Even after so many years, we can’t say which protocol is best over another. All it depends on your business requirement, understanding, behavior of deployed applications and network design. So decision is absolutely yours.
People who read this post also read :
- Which Routing Protocol To Select? OSPF Vs EIGRP
- What is Discard Route or NULL0 Route?
- OSPF Fast Convergence Tools - Updating RIB
- OSPF Fast Convergence Tools - Event Processing
- OSPF Fast Convergence Tools - Event Propagation
- OSPF Fast Convergence Tools
- How does OSPF behave with SSO,NSF and NSR
- OSPF High Availability with SSO,NSF and NSR
- OSPF Routing Protocol Summary
- OSPF LSA and Packet Format
- Bidirectional Forwarding Detection
- Free Online CCNA - OSPF Labs
- OSPF Sham Link In Different Area
- IGP Interview Questions For CCNA and CCNP Engineers
- OSPF External Routes Not Redistributing
- Non Zero Forwarding Address In LSA 5
- Opaque LSA Brought Router Down
- External LSA 5
- OSPF: Link State Advertisement (LSA) - 4
- OSPF: Link State Advertisement (LSA) - 3
- OSPF: Link State Advertisement (LSA) - 2
- OSPF: Link State Advertisement (LSA) - 1
- Eradicate OSPF External Routes
- OSPF Routes Are Not Installing At CPE Router
- BGP As PE-CE With Backboor Link Part 2
Wednesday, December 19, 2012
Route Redistribution Basics: Golden Rules about Route Redistribution
2. The redistributing protocol knows which routes to take from the RIB based on the “known via” information present in "show ip route" details.
3. A route must be installed in the RIB for it to be redistributed in another protocol.
4. Routes redistributed from the routing table are not re-installed again into the RIB.
5. Only the attributes of a route present in the RIB can be used for filtering.
Redistribution Filters:-
1. Redistribution filters can control what information is injected into a routing protocol through redistribution.
2. Filters can also be used to stop routing loops(Read more about layer 3 routing loops) when mutual redistribution between two routing protocols is configured.
Redistribution Filter Tools:-
1. Match metric:- Filtering is possible between all protocols based on metric used.
2. Match Tag:- While mutual redistribution, TAGs can be assigned to routes to stop the routing loop too.
3. Match IP Address:- Matches the prefix, possibly the network mask, depending on the access list type used.
4. Match IP Next Hop Address:- Matches on the next hop listed in the routing table.
5. Match route-type
6. Match Interface
Tuesday, December 18, 2012
Basics of Static Routing: Secret Facts about Static Routing
1.Static routes can have next hop address of an IP Address:-
ip route 10.2.2.0 255.255.255.0 10.1.2.1. Defining this type of route causes the RIB and CEF to recursively lookup the correct layer 2 header to rewrite onto the packet. As long as the next hop is reachable, the router assumes the destination through that next hop is reachable.
2.Static routes can have next hop address as point to point interface address:- ip route 10.2.2.0 255.255.255.0 serial0. The RIB and CEF point the route directly at the point-to-point interface. For each packet destined to 10.2.2.0/24, the layer 2 rewrite header is set up to reach the other end of the point-to-point link. As long as the interface is up, the router assumes the destination is reachable through that interface.
3.Static routes can have next hop address as broadcast interface:- ip route 10.2.2.0 255.255.255.0 fa0/0. If you point a static route to a broadcast interface, the route is inserted into the routing table only when the broadcast interface is up. This configuration is not recommended because when the next hop of a static route points to an interface, the router considers each of the hosts within the range of the route to be directly connected through that interface. With this configuration, router assumes all the interfaces are directly connected and performs the ARP request for every destination. This configuration increases the IP Input and consumes lot of memory to store the arp entries. This configuration requires enabling proxy ARP on routers, if it is not enabled will lead to drop the packets.
For default routes with outgoing interface as broadcast interface could lead to 2 raise to power 32 entries in the ARP table.
ABOUT AUTHOR: Shivlu jain
Thursday, December 13, 2012
Basics of EIGRP Routing Protocol: EIGRP Cheatsheet – Learn EIGRP in 15 min
Source: PROHACK

About the author : Rishabh Dangwal
Friday, October 5, 2012
CBT Nuggets - Juniper Networks Junos Associate JN0-101-PLATO | ISO | 1.06 GB
Genre: Video Training
http://extabit.com/file/2aj2mdcmw0djs/CBT.Nuggets.Juniper.Networks.Junos.Associate.JN0101PLATO.rar
Lumfile:
http://lumfile.com/ly0v1x2lcefs/CBT.Nuggets.Juniper.Networks.Junos.Associate.JN0101PLATO.rar.html
Uploaded:
http://uploaded.net/file/qpgc02f2/CBT.Nuggets.Juniper.Networks.Junos.Associate.JN0101PLATO.rar
Thursday, March 15, 2012
How LSA Works with/without OSPF AREA 0 | Running OSPF without AREA 0 By Anuj Tyagi: Case Study
Hi Friends, I have received a complete case study done by Mr.Anuj Tyagi on OSPF routing protocol. After reading our article Configure OSPF without AREA 0: CCNP OSPF Case Study, he also tested the similar scenario in his testing LAB. I am publishing his case study as it is without any editing so that guys who are learning networking & OSPF, will get some benefit from this.
Running OSPF without AREA 0
Topology 1: Connecting OSPF Area 2 and area 3 without using ABR.
Interface configurations are mentioned above in the topology.
Remember,
· ABR: ABR is a area border router that contain interfaces in atleast two separate area out of which one should always be in AREA 0.
So, surely above topology don’t have any ABR and we will be going to test how routers behavior in absence of backbone area.
After configuring OSPF routes on R1, R2, R3 as in above topology, we analysis all Routers neighbor table .
That shows Full Neighborship Status for neighbors . Take a look again at the neighbor table,
Neighborship is being maintained with it’s directly connected interfaces.
Now, if we will try to PING
· R2 S0/1 , surely we will get successful reply .
· R2 S0/0, we will get successful reply (as it is directly connected)
· R3 S0/0, obviously we R1 can’t reach 2.2.2.1 of R2 we will be unable to get reply from R3 s0/0.
Why? Just take a look at the neighborship table of R1 again .
So, what is happening behind the scenes when R1 trying to communicate with 2.2.2.0/24 network .
R1 can’t even find the path or from which interface R1 should send the packets .
Now lets take a look at the Router OSPF LSA’s,
· R1 having LSA1 (router-id) updates of only those routers in same area.
Reason : There is no ABR to send LSA3 (summary LSA) updates . ( remember ABR? )
After looking at LSA and neighbor-table, you can guess about the routes will be there in Routing Table.
Again, they are also from directly connected interfaces with Routers.
Now make it a bit interesting, we will going to add interfaces on R2 in Area 0 .
Now, compare neighborship table of Router R1,R2,R2 with and without AREA 0 (backbone area) .
R1 topology table with AREA 0
We can now clearly see LSA3 in the table, apart from networks of Area 0 R1 got one more network advertisement in LSA for 192.168.2.0/24 and 2.2.2.0/24 in summary LSA updates from R2(ABR router).
While in
R2 topology table without AREA 0
In the same way, AREA 0 will also make Router R2 as ABR now and that will add a lot to topology table of Router R2 .
Now, it is behaving like ABR as it is acting as both in AREA-2 and AREA-3 completely.
Router R3 also getting LSA1 and LSA3 updates from R2(ABR).
Note: LSA2 updates (network LSA) are only advertised in Non-broadcast where DR & BDR exist.
Now , also PING will be successful from any Router to any network in topology.
Conclusion:
OSPF will not form neighborship with inter-area(IA) routes if there is no backbone area exist or we do not use ABR . In other words, Each area share it’s link state database only through AREA0 to any other AREA. It will make neighborship only with directly connected networks
LSA 1,2 do not need Area0 to share it’s Acknowledgement but LSA2 will form only in non-broacast network (like frame-relay) where DR will be having responsibility to send updates but we must need to have AREA0 to send LSA 3, 4, 5 & 7 updates.
----------------------------------------------------------------------------
R1 Config
Using 1024 out of 57336 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
ip cef
!
!
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
multilink bundle-name authenticated
!
!
archive
log config
hidekeys
!
!
!
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
duplex auto
speed auto
!
interface Serial0/0
ip address 1.1.1.1 255.255.255.0
clock rate 2000000
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
router ospf 100
router-id 1.1.1.1
log-adjacency-changes
network 1.1.1.0 0.0.0.255 area 2
network 192.168.1.0 0.0.0.255 area 2
!
ip forward-protocol nd
!
!
ip http server
no ip http secure-server
!
!
line con 0
line aux 0
line vty 0 4
!
!
end
-------------------------------------------------------------
R2-ABR Config
R2-ABR#show configuration
Using 1114 out of 57336 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
ip cef
!
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
multilink bundle-name authenticated
!
!
archive
log config
hidekeys
!
!
interface FastEthernet0/0
ip address 172.16.1.1 255.255.0.0
duplex auto
speed auto
!
interface Serial0/0
ip address 1.1.1.2 255.255.255.0
clock rate 2000000
!
interface FastEthernet0/1
ip address 172.17.1.1 255.255.0.0
duplex auto
speed auto
!
interface Serial0/1
ip address 2.2.2.1 255.255.255.0
clock rate 2000000
!
router ospf 100
router-id 2.2.2.2
log-adjacency-changes
network 1.1.1.0 0.0.0.255 area 2
network 2.2.2.0 0.0.0.255 area 3
network 172.16.0.0 0.0.255.255 area 0
network 172.17.0.0 0.0.255.255 area 0
!
ip forward-protocol nd
!
!
ip http server
no ip http secure-server
!
!
control-plane
!
!
line con 0
line aux 0
line vty 0 4
!
!
end
-------------------------------------------------------------------------
R3 Config
Using 1024 out of 57336 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
ip cef
!
!
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
multilink bundle-name authenticated
!
!
!
!
archive
log config
hidekeys
!
!
!
interface FastEthernet0/0
ip address 192.168.2.1 255.255.255.0
duplex auto
speed auto
!
interface Serial0/0
ip address 2.2.2.2 255.255.255.0
clock rate 2000000
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
router ospf 100
router-id 3.3.3.3
log-adjacency-changes
network 2.2.2.0 0.0.0.255 area 3
network 192.168.2.0 0.0.0.255 area 3
!
ip forward-protocol nd
!
!
ip http server
no ip http secure-server
!
control-plane
!
!
!
line con 0
line aux 0
line vty 0 4
!
!
end
Wednesday, March 14, 2012
What is CEF- Cisco Express Forwarding: Load-Balancing with Static Routing
What is CEF- Cisco Express Forwarding: Load-Balancing with Static Routing
The topology is given below we will be using here :
We made loopbacks each on R1& R2 and configure default static-routing with next hop interfaces on R2.
Configuration is like this :
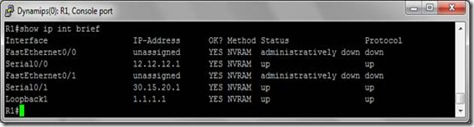
On R1:
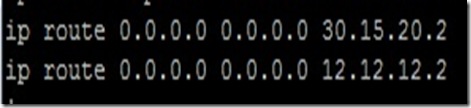
Configuring Default-routes on R1:
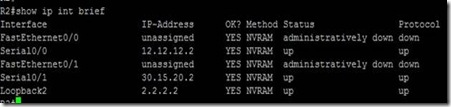
On R2:
Now we did trace route from R1 to Loopback 2.2.2.2 on R2 :
Take a look … it is sending one packet from 12.12.12.0/24 network and other from
And this is what R1 shows but what’s happening behind the scenes on R2 ?
Enabling Debug ip packet on R2 will help to know the sources of packets.
So, this is interesting ….
It shows,
For one packet source is 12.12.12.1 (interface S0/0)
And for another 30.15.20.1 (interface S0/1) and the process take place like this and packets has been sent from each serial interface of R1 alternatively.
But here’s the catch ….
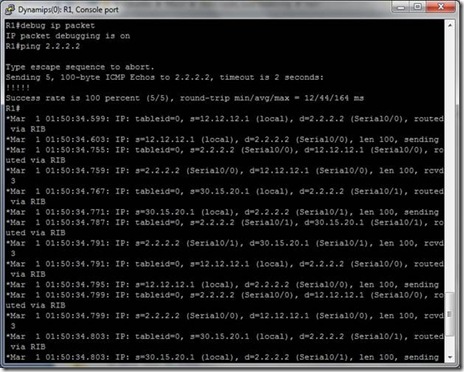
With trace route load-balancing is working fine but when I tried with PING to 2.2.2.2
And as usual #debug ip packets was enabled on R2 . Things are not in favor now L
They are only using same route to send and receive packets.
And at the same time on R1
Note: Routed packets via FIB …
I saw it is following only 30.15.20.0/24 network to send packets. No load balancing.
Look at the above picture carefully,
When R1 is sending packet s=30.15.20.1 , d=2.2.2.2, routed through RIB.
And When R2 is sending Acknowledgement reply for this packet when s=2.2.2.2 and d=30.15.20.1, routed via FIB.
Mummble …. Now whats that CEF, FIB, RIB ??
RIB - routing information base
FIB - forwarding information base
CEF- Cisco Express Forwarding
Once CEF is enabled, it will form the FIB table with the help of Routing table. Now router no longer looks on RIB and FIB acts as replacement for RIB.
CEF also generates adjacency table which pre-maps all of the next hop ip as well as MAC address so as we configure Static routing, CEF add routes to FIB (forwarding information base) and send the packets through the interface which is added first into the table and the static route we have configured first will be added first and will be used to send packets .
Since, here 30.15.20.0/24 is stored first as well as configured first for static route so it will be using 30.15.20.0/24
At the same moment and it will not check the routing table when sending packets to another router/network from then on unless there is change in the routing table and will forward all the packets based on CEF table only.
CEF is ON by default on the routers.
Now, try to debug after Disabling CEF on R1
We are successful to load-balance equally from R1-R2 by disabling CEF. J
NOTE: Routed via RIB not FIB i.e. No longer using FIB table created by CEF.
Now, why?? Why ?? traceroute is able to do load-balancing without disabling CEF ?
Better to find out through practical approach
CEF is enable (by default)
Enable #debug ip packet and
Traceroute to 2.2.2.2
Note : sending broad/multicast .
Now, why it was choosing 30.15.20.0/24 not 12.12.12.10/24 network when we are sending packets through PING??
Hope this is informative for you .
Thank you for reading.
















![clip_image013[1] clip_image013[1]](http://lh3.ggpht.com/--Pl2ctzHHWo/TjAMQp78-yI/AAAAAAAAGQ0/i175IcRTS54/clip_image013%25255B1%25255D_thumb%25255B1%25255D.jpg?imgmax=800)