The Browser Exploitation Framework (BeEF) is a penetration testing tool written in Ruby and designed to both showcase browser weaknesses as well as perform attacks both on and through the web browser. BeEF consists of a server application that manages the connected clients, known as “zombies”, and JavaScript “hooks” which run in the browser of target hosts.
Traditionally, the JavaScript hook is injected by the attacker into HTML code either through an attack such as Cross Site Scripting (XSS) or SQL Injection. Once the hook is processed by the browser, it beacons back home to the BeEF server, and will process JavaScript based commands sent from the BeEF server to the client.
The commands sent to the browser are triggered through modules running within the BeEF server. These modules send commands that do everything from fingerprinting browsers and plug-ins to allowing the attacker to proxy web traffic through the browser. Additional modules exist to perform tasks such as network scanning, browser keystroke logging, and cross protocol exploitation where HTTP requests can be sent to non-HTTP services with exploit payloads that will execute and return shells back to an attacker.
In backtrack Beef has been installed.But it`s not latest version , so you have to clone git repository for latest installation.
git clone https://github.com/beefproject/beef.git
cd beef
gem install bundler
bundle install
./beef
Open user interface URL in brwoser & enter username & password which is beef. On the right side you can see getting started text & log.
Now what you have to do is just send link http://your I.P:3000/demos/butcher/index.html or http://your I.p.:3000/demos/basic.html to victim
You can also put it in iframe and make some fake website & send link of fake website to victim like Metasploit Browser Exploitation method.
As soon as victim click on your link ; you can see victim I.P. on online browser in left side of panel.
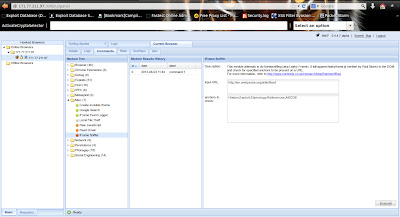
Now click on I.P. & then command tab on righ side . There is list of command which you can execute on victim browser as long as he has open our link in his browser.
Here you can see three section module tree ; result history & details about module .
Select module & click on execute button & then view command result in module history.
There is lots of module available ; you can test it one by one & find some intresting info about victim.But our main requirement is victim should keep open our link.
Traditionally, the JavaScript hook is injected by the attacker into HTML code either through an attack such as Cross Site Scripting (XSS) or SQL Injection. Once the hook is processed by the browser, it beacons back home to the BeEF server, and will process JavaScript based commands sent from the BeEF server to the client.
The commands sent to the browser are triggered through modules running within the BeEF server. These modules send commands that do everything from fingerprinting browsers and plug-ins to allowing the attacker to proxy web traffic through the browser. Additional modules exist to perform tasks such as network scanning, browser keystroke logging, and cross protocol exploitation where HTTP requests can be sent to non-HTTP services with exploit payloads that will execute and return shells back to an attacker.
In backtrack Beef has been installed.But it`s not latest version , so you have to clone git repository for latest installation.
git clone https://github.com/beefproject/beef.git
cd beef
gem install bundler
bundle install
./beef
Open user interface URL in brwoser & enter username & password which is beef. On the right side you can see getting started text & log.
Now what you have to do is just send link http://your I.P:3000/demos/butcher/index.html or http://your I.p.:3000/demos/basic.html to victim
You can also put it in iframe and make some fake website & send link of fake website to victim like Metasploit Browser Exploitation method.
As soon as victim click on your link ; you can see victim I.P. on online browser in left side of panel.
Now click on I.P. & then command tab on righ side . There is list of command which you can execute on victim browser as long as he has open our link in his browser.
Here you can see three section module tree ; result history & details about module .
Select module & click on execute button & then view command result in module history.
There is lots of module available ; you can test it one by one & find some intresting info about victim.But our main requirement is victim should keep open our link.

No comments:
Post a Comment